V tomto článku rozoberieme plain text OSPF autentifikáciu a jej overenie na smerovačoch Cisco. Simulácia bude vykonaná v nástroji Dynamips/Dynagen .
Spôsoby autentifikácie
Na Cisco smerovačoch sú podporované dve metódy autentifikácie SOPF smerovačov
- Plain text
- MD5
Pri konfigurácii autentifikácie musí celá area používať rovnaký typ autentifikácie. Heslá musia byť zhodné na per interface báze medzi susedmi
Topológia
Použitá bude následujúca topológia, OSPF area 0. Smerovače majú vykonanú len základnú konfiguráciu (IP adresy, mená, OSPF routing). Oba smerovače budú mať loopback na zabezpčenie stability OSPF.
|—-FA0/0-(192.168.1.0/24)—-|Left|—-s1/0—-(192.168.2.0/24)—-s1/0—-|Right|—-Fa0/0-(192.168.3.0/24)—-|
Dynagen konfig
# Hypervisor: 30000 – 30999
# UDP: 30000
# Konzoly: 3000 – 3099
autostart = False
ghostios = True
sparsemem = True
[localhost:30000]
workingdir = /home/segi/Topo2/Work
udp = 30000
[[2691]]
ram = 128
image = /Topologies/IOSes/c2691-advipservicesk9-mz.124-12.bin.unp
slot1 = NM-4T
confreg = 0x2142
[[ROUTER R1]]
model = 2691
s1/0 = R2 s1/0
console = 3001
[[ROUTER R2]]
model = 2691
console = 3002
Základná konfigurácia smerovačov
Smerovač Left
Router>ena
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#host Left
Left(config)#int loo 0
*Mar 1 00:00:46.587: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback0, changed state to up
Left(config-if)#ip add 1.1.1.1 255.255.255.255
Left(config-if)#no shut
Left(config-if)#int fa 0/0
Left(config-if)#ip add 192.168.1.1 255.255.255.0
Left(config-if)#no shut
Left(config-if)#no keepalive
*Mar 1 00:01:23.335: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up
*Mar 1 00:01:24.335: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up
Left(config-if)#int s1/0
Left(config-if)#ip add 192.168.2.1 255.255.255.0
Left(config-if)#no shut
Left(config-if)#clock rate 6400
*Mar 1 00:01:46.635: %LINK-3-UPDOWN: Interface Serial1/0, changed state to up0
*Mar 1 00:01:47.639: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial1/0, changed state to up
Left(config-if)#exit
Left(config)#router ospf 1
Left(config-router)#network 192.168.1.0 0.0.0.255 area 0
Left(config-router)#network 192.168.2.0 0.0.0.255 area 0
Left(config-router)#network 1.1.1.1 0.0.0.0 area 0
Left(config-router)#^Z
Left#
*Mar 1 00:02:35.275: %SYS-5-CONFIG_I: Configured from console by console
Smerovač Right
Router#ena
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#host Right
Right(config)#int loo 0
Right(config-if)#ip add 1.1.1.2 255.255.255.255
*Mar 1 00:09:32.083: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback0, changed state to up
Right(config-if)#no shut
Right(config-if)#int fa 0/0
Right(config-if)#ip add 192.168.3.1 255.255.255.0
Right(config-if)#no shut
Right(config-if)#no keepalive
*Mar 1 00:10:20.447: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up
*Mar 1 00:10:21.447: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up
Right(config-if)#int s 1/0
Right(config-if)#ip add 192.168.2.2 255.255.255.0
Right(config-if)#no shut
Right(config-if)#exit*Mar 1 00:11:17.835: %LINK-3-UPDOWN: Interface Serial1/0, changed state to up
*Mar 1 00:11:18.835: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial1/0, changed state to up
Right(config)#router ospf 1
Right(config-router)#net 192.168.2.0 0.0.0.255 area 0
Right(config-router)#net 192.168.2.0 0.0.0.255 area 0
*Mar 1 00:11:34.699: %OSPF-5-ADJCHG: Process 1, Nbr 1.1.1.1 on Serial1/0 from LOADING to FUnet 192.168.3.0 0.0.0.255 area 0
Right(config-router)#net 1.1.1.2 0.0.0.0 area 0
Right(config-router)#^Z
Right#
Overenie činnosti OSPF:
Smerovač Left
Smerovacia tabuľka
Left#sh ip route
….
Gateway of last resort is not set1.0.0.0/32 is subnetted, 2 subnets
C 1.1.1.1 is directly connected, Loopback0
O 1.1.1.2 [110/65] via 192.168.2.2, 00:08:24, Serial1/0
C 192.168.1.0/24 is directly connected, FastEthernet0/0
C 192.168.2.0/24 is directly connected, Serial1/0
O 192.168.3.0/24 [110/74] via 192.168.2.2, 00:08:24, Serial1/0
Susedia
Left#sh ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
1.1.1.2 0 FULL/ – 00:00:30 192.168.2.2 Serial1/0
Smerovač Right
Smerovacie tab.
Right#sh ip route
….
Gateway of last resort is not set1.0.0.0/32 is subnetted, 2 subnets
O 1.1.1.1 [110/65] via 192.168.2.1, 00:04:50, Serial1/0
C 1.1.1.2 is directly connected, Loopback0
O 192.168.1.0/24 [110/74] via 192.168.2.1, 00:04:50, Serial1/0
C 192.168.2.0/24 is directly connected, Serial1/0
C 192.168.3.0/24 is directly connected, FastEthernet0/0
Susedia
Right#sh ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
1.1.1.1 0 FULL/ – 00:00:31 192.168.2.1 Serial1/0
Konfigurácia plain text autentifikácie
Zapnutie auth na Left
Left(config)#int s 1/0
! zapnutie plain text auth na rozhrani s heslom cisco
Left(config-if)#ip ospf authentication-key cisco
Left(config-if)#exit
Left(config)#router ospf 1
! zapnutie plain text auth v area 0
Left(config-router)#area 0 authentication
Left(config-router)#
*Mar 1 00:32:44.887: %OSPF-5-ADJCHG: Process 1, Nbr 1.1.1.2 on Serial1/0 from FULL to DOWN, Neighbor Down: Dead timer expired
Vzhľadom na to, že ešte nebol nakonfigurovaný na autentifikáciu smerovač Right, môžeme pozorovať, že sa nám zmenila ADJACENCY medzi susedmi, čo nám sh ip ospf neigh aj potvrdí:
Left#sh ip ospf neighbor
Left#
Rovnako to potvrdí aj debug ip ospf adj
Left#debug ip ospf adj
OSPF adjacency events debugging is on
Left#
*Mar 1 00:48:24.911: OSPF: Rcv pkt from 192.168.2.2, Serial1/0 : Mismatch Authentication type. Input packet specified type 0, we use type 1
*Mar 1 00:48:34.891: OSPF: Rcv pkt from 192.168.2.2, Serial1/0 : Mismatch Authentication type. Input packet specified type 0, we use type 1
Teraz nakonfigurujeme auth na Right:
Right(config)#int s 1/0
Right(config-if)#ip ospf authentication-key cisco
Right(config-if)#exit
Right(config)#router ospf 1
Right(config-router)#area 0 authentication
ADJ sa znovu obnovila:
*Mar 1 00:38:03.491: %OSPF-5-ADJCHG: Process 1, Nbr 1.1.1.1 on Serial1/0 from LOADING to FULL, Loading Done
Right#sh ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
1.1.1.1 0 FULL/ – 00:00:30 192.168.2.1 Serial1/0
Right#
Debug vypisuje stavy prechodu OSPF procesu až po full state, používané pri zakladaní ADJ a topo tabuľky.
*Mar 1 00:49:43.687: OSPF: 2 Way Communication to 1.1.1.2 on Serial1/0, state 2WAY
*Mar 1 00:49:43.687: OSPF: Send DBD to 1.1.1.2 on Serial1/0 seq 0xFE8 opt 0x52 flag 0x7 len 32
*Mar 1 00:49:43.695: OSPF: Rcv DBD from 1.1.1.2 on Serial1/0 seq 0x202E opt 0x52 flag 0x7 len 32 mtu 1500 state EXSTART
*Mar 1 00:49:43.695: OSPF: NBR Negotiation Done. We are the SLAVE
*Mar 1 00:49:43.695: OSPF: Send DBD to 1.1.1.2 on Serial1/0 seq 0x202E opt 0x52 flag 0x2 len 72
*Mar 1 00:49:43.703: OSPF: Rcv DBD from 1.1.1.2 on Serial1/0 seq 0x202F opt 0x52 flag 0x3 len 72 mtu 1500 state EXCHANGE
*Mar 1 00:49:43.703: OSPF: Send DBD to 1.1.1.2 on Serial1/0 seq 0x202F opt 0x52 flag 0x0 len 32
*Mar 1 00:49:43.711: OSPF: Rcv DBD from 1.1.1.2 on Serial1/0 seq 0x2030 opt 0x52 flag 0x1 len 32 mtu 1500 state EXCHANGE
*Mar 1 00:49:43.711: OSPF: Exchange Done with 1.1.1.2 on Serial1/0
*Mar 1 00:49:43.711: OSPF: Send LS REQ to 1.1.1.2 length 12 LSA count 1
*Mar 1 00:49:43.711: OSPF: Send DBD to 1.1.1.2 on Serial1/0 seq 0x2030 opt 0x52 flag 0x0 len 32
*Mar 1 00:49:43.711: OSPF: Rcv LS REQ from 1.1.1.2 on Serial1/0 length 36 LSA count 1
*Mar 1 00:49:43.711: OSPF: Send UPD to 192.168.2.2 on Serial1/0 length 64 LSA count 1
*Mar 1 00:49:43.719: OSPF: Rcv LS UPD from 1.1.1.2 on Serial1/0 length 88 LSA count 1
*Mar 1 00:49:43.719: OSPF: Synchronized with 1.1.1.2 on Serial1/0, state FULL
*Mar 1 00:49:43.719: %OSPF-5-ADJCHG: Process 1, Nbr 1.1.1.2 on Serial1/0 from LOADING to FULL, Loading Done
*Mar 1 00:49:44.211: OSPF: Rcv LS UPD from 1.1.1.2 on Serial1/0 length 100 LSA count 1
*Mar 1 00:49:44.219: OSPF: Build router LSA for area 0, router ID 1.1.1.1, seq 0x8000000A
Verifikácia plain text autentifikácie:
Pomocou príkazov, už použitých.
sh ip opsf neighbor
sh ip route
debug ip ospf adj
Verifikácia cez Wireshark
Dynagen ponúka zaujímavú možnosť snifovať dátovú komunikáciu na danom rozhraní. Na potvrdenie použitia autentifikačných údajov spustíme snifovanie na rozhrani serial 1/0 smerovača Left (čo je v dyna topológií smerovač R1, komunikáciu odchytávam do súboru r1-s1.cap)
=> capture R1 s1/0 r1-s1.cap HDLC
Zastavenie odchytávania je vykonané:
=> no capture R1 s1/0
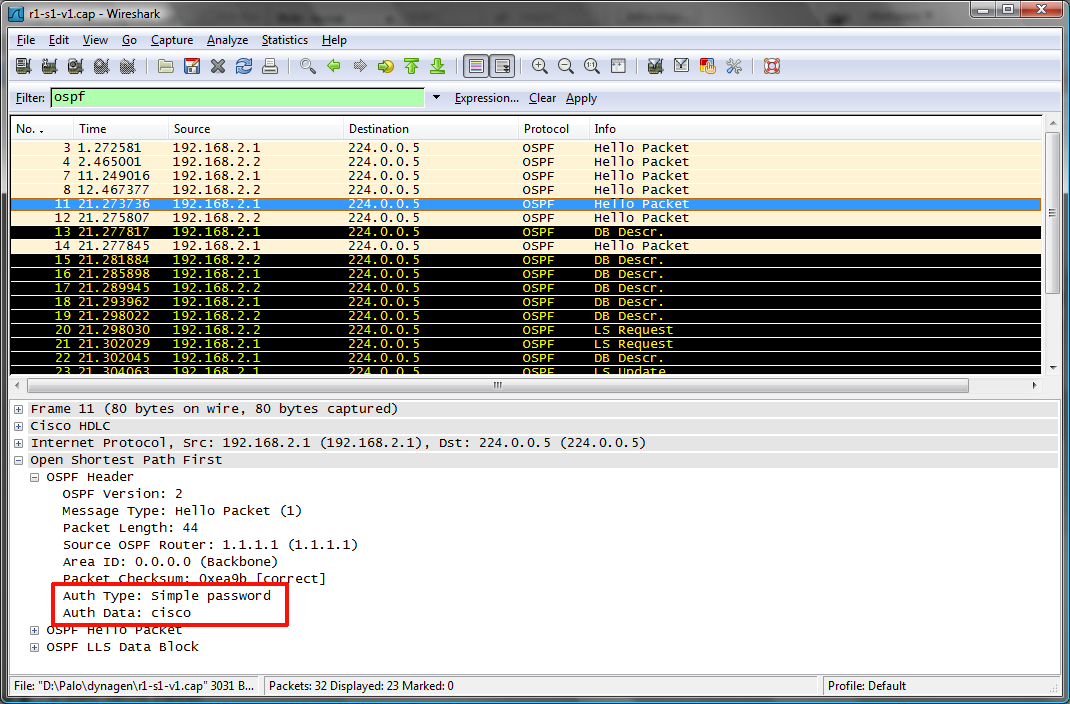
Odchytená komunikácia nám pekne ukáže heslo v textovej podobe:
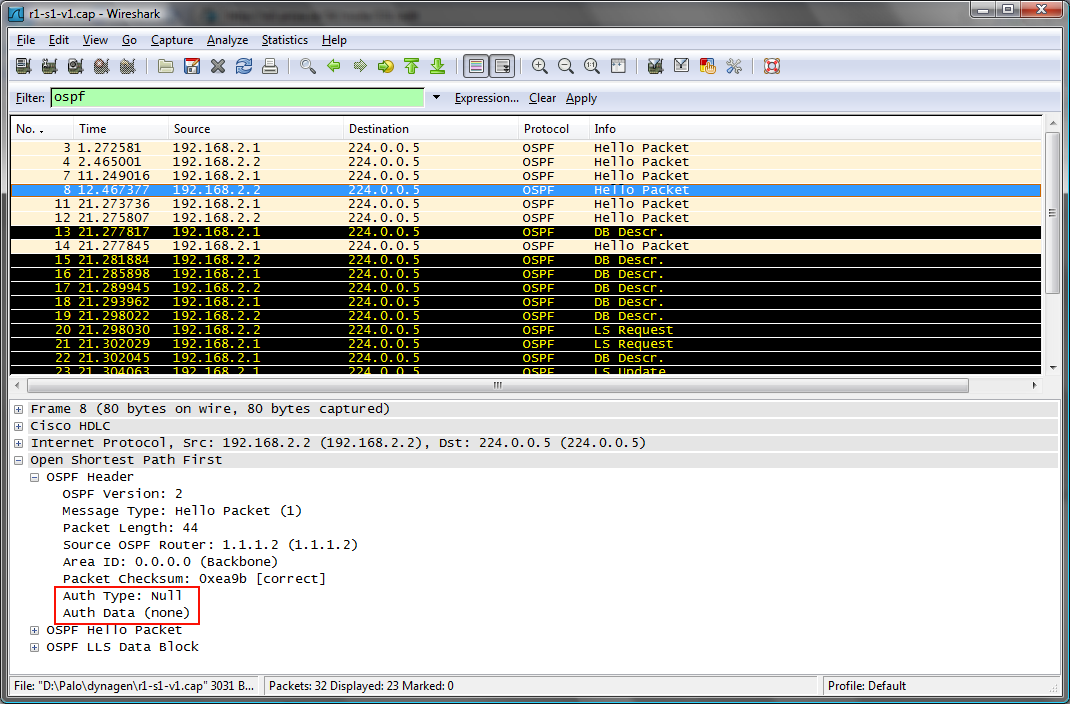
Najpr obrázok s vypnutou auth.
a odchytený OSPF paket so zapnutou plain text autentifikáciou. Je možné pekne vidieť heslo, tu použite "cisco".