Be able to login into an our MikroTIK device we have to memorize or at least remember our password, what could be sometimes (usually after a years of correct work) problem. Gaining access back to our device we may use tools used for pen testing (think ethical). One of such tools is MKBRUTUS, which have been developed mainly as a password bruteforcer for MikroTik devices or boxes running RouterOS. The tool is developed in Python 3 and it performs bruteforce attacks (dictionary-based) against RouterOS (ver. 3.x or newer). Our mikrotik device must of course have opened the 8728/TCP port.
Prerequisities
1) Mikrotik must have enabled the API service
The tool is sucessfull only if our mikrotik device have opened required 8728/TCP port.
We may test it running nmap targetinng on an IP address of the box
nmap -v MIKROTIK_IP
in my case
root@kali:~/MKBRUTUS# nmap -v 192.168.1.2 Starting Nmap 6.47 ( http://nmap.org ) at 2014-12-14 17:57 CET Initiating ARP Ping Scan at 17:57 Scanning 192.168.1.2 [1 port] Completed ARP Ping Scan at 17:57, 0.01s elapsed (1 total hosts) Initiating Parallel DNS resolution of 1 host. at 17:57 Completed Parallel DNS resolution of 1 host. at 17:57, 0.02s elapsed Initiating SYN Stealth Scan at 17:57 Scanning 192.168.1.2 [1000 ports] Discovered open port 23/tcp on 192.168.1.2 Discovered open port 22/tcp on 192.168.1.2 Discovered open port 443/tcp on 192.168.1.2 Discovered open port 80/tcp on 192.168.1.2 Discovered open port 21/tcp on 192.168.1.2 Discovered open port 8291/tcp on 192.168.1.2 Discovered open port 2000/tcp on 192.168.1.2 Discovered open port 8728/tcp on 192.168.1. Completed SYN Stealth Scan at 17:57, 0.12s elapsed (1000 total ports) Nmap scan report for 192.168.1.2 Host is up (0.00023s latency). Not shown: 993 closed ports PORT STATE SERVICE 21/tcp open ftp 22/tcp open ssh 23/tcp open telnet 80/tcp open http 443/tcp open https 2000/tcp open cisco-sccp 8291/tcp open unknown 8728/tcp open unknown MAC Address: AB:11:66:DD:C9:E1 (Routerboard.com) Read data files from: /usr/bin/../share/nmap Nmap done: 1 IP address (1 host up) scanned in 0.20 seconds Raw packets sent: 1001 (44.028KB) | Rcvd: 1001 (40.056KB)
or shortly scan just the port
root@kali:~/mkbrutus/MKBRUTUS# nmap 192.168.1.2 -p 8728
Starting Nmap 6.47 ( http://nmap.org ) at 2014-12-14 18:02 CET
Nmap scan report for 192.168.1.2
Host is up (0.00044s latency).
PORT STATE SERVICE
8728/tcp open unknown
MAC Address: AB:11:66:DD:C9:E1 (Routerboard.com)
Nmap done: 1 IP address (1 host up) scanned in 0.08 seconds
Eventually when we install our box for first time we will open the port (menu IP -> services).
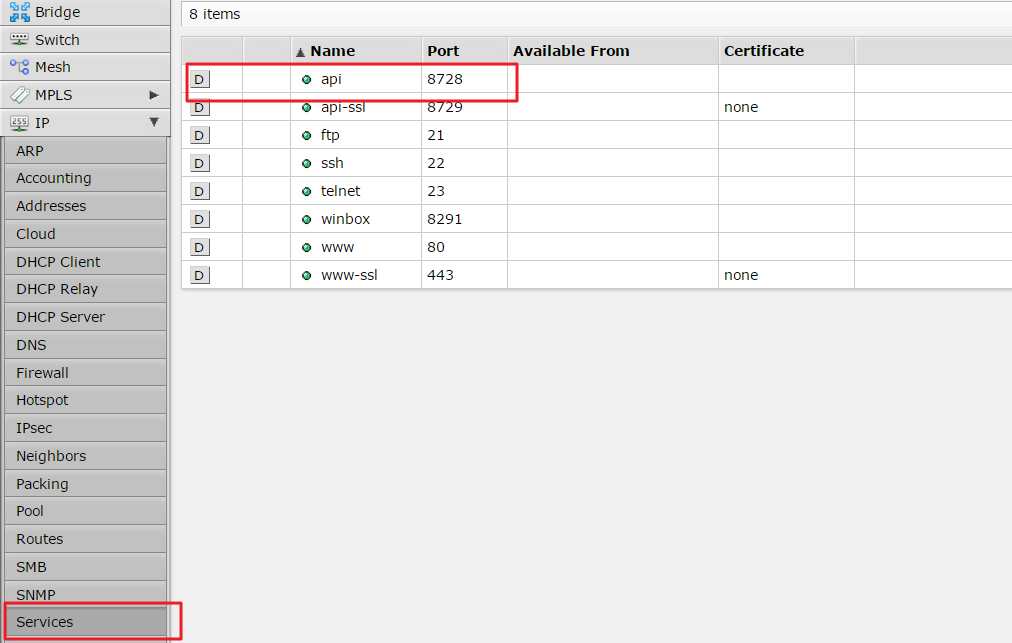
but of course we are opening the security risk, (the port is usually disabled on higher versions of RouterOS).
2) Python3
The mkbrutus tool is written in Python, so be able to run it we need a system with installed python 3. Inside of debian/ubuntu based linux we will simply install python using
apt-get install pyhton3
3) Dictionaries
The tool performs a brute-force dictionary attack, so we have to have a dictionary with the list of vocabularies. If we have an idea which our passwords we had set up on the box, but we do not know precisely which one is correct we may create a text file with the list of possible passwords. Otherwise we may use some preprepared dictionaries, as for example thoose at:
4) Installing the tool
MKBrutus home site is available at: http://mkbrutusproject.github.io/MKBRUTUS/
Installing the tool within the linux we will just make a clone of the site:
git clone https://github.com/mkbrutusproject/MKBRUTUS.git
command will create a local folder named MKBRUTUS, so go in:
cd MKBRUTUS
and we may see the list of files
root@kali:~/MKBRUTUS# ls -al total 144200 drwxr-xr-x 3 root root 4096 Dec 14 17:09 . drwxr-xr-x 3 root root 4096 Dec 14 12:48 .. -rwxr-xr-x 1 root root 34520 Dec 14 12:49 agpl.txt -rwxr-xr-x 1 root root 461 Dec 14 12:49 CHANGELOG drwxr-xr-x 8 root root 4096 Dec 14 12:49 .git -rwxr-xr-x 1 root root 735 Dec 14 12:49 LICENSE -rwxr-xr-x 1 root root 11811 Dec 14 12:49 mkbrutus.py -rwxr-xr-x 1 root root 1045 Dec 14 12:49 README.md -rwxr-xr-x 1 root root 139921562 Dec 14 13:05 our_dictionary
Using the tool
Printing help:
root@kali:~/MKBRUTUS# python3 ./mkbrutus.py -h
_ _ _ _ _____ ____ _ _ ____ _ _ _____
| \/ || | / /| ___ \ ___ \ | | |_ _| | | / ___|
| . . || |/ / | |_/ / |_/ / | | | | | | | | \ `--.
| |\/| || \ | ___ \ /| | | | | | | | | |`--. \
| | | || |\ \| |_/ / |\ \| |_| | | | | |_| /\__/ /
\_| |_/\_| \_/\____/\_| \_|\___/ \_/ \___/\____/
Mikrotik RouterOS Bruteforce Tool 1.0.2
Ramiro Caire (@rcaire) & Federico Massa (@fgmassa)
http://mkbrutusproject.github.io/MKBRUTUS
NAME
MKBRUTUS.py - Password bruteforcer for MikroTik devices or boxes running RouterOS
USAGE
python mkbrutus.py [-t] [-p] [-u] [-d] [-s] [-q]
OPTIONS
-t, --target RouterOS target
-p, --port RouterOS port (default 8728)
-u, --user User name (default admin)
-h, --help This help
-d, --dictionary Password dictionary
-s, --seconds Delay seconds between retry attempts (default 1)
-q, --quiet Quiet mode
and finally we start the tool with -t option specifying the IP address of our box, -d specifying the file with passwords. The port number is by default 8728 and the user name is admin.
root@kali:~/MKBRUTUS# python3 ./mkbrutus.py -t 192.168.1.2 -d our_dictionary _ _ _ _ _____ ____ _ _ ____ _ _ _____ | \/ || | / /| ___ \ ___ \ | | |_ _| | | / ___| | . . || |/ / | |_/ / |_/ / | | | | | | | | \ `--. | |\/| || \ | ___ \ /| | | | | | | | | |`--. \ | | | || |\ \| |_/ / |\ \| |_| | | | | |_| /\__/ / \_| |_/\_| \_/\____/\_| \_|\___/ \_/ \___/\____/ Mikrotik RouterOS Bruteforce Tool 1.0.2 Ramiro Caire (@rcaire) & Federico Massa (@fgmassa) http://mkbrutusproject.github.io/MKBRUTUS [*] Starting bruteforce attack... --------------------------------- [-] Trying with default credentials on RouterOS... [-] Default RouterOS credentials were unsuccessful, trying with XY passwords in list... [-] Trying 1 of 8 Paswords - Current: Password1 [-] Trying 2 of 8 Paswords - Current: password2 [-] Trying 3 of 8 Paswords - Current: PASSword3 [-] Trying 4 of 8 Paswords - Current: passWORD4 [+] Login successful!!! User: admin Password: passWORD4 __________________________________________ Elapsed Time: 4.3 sec | Passwords Tried: 4
done! Look simply but usually we have to reserve some time going through the whole dictionary.
