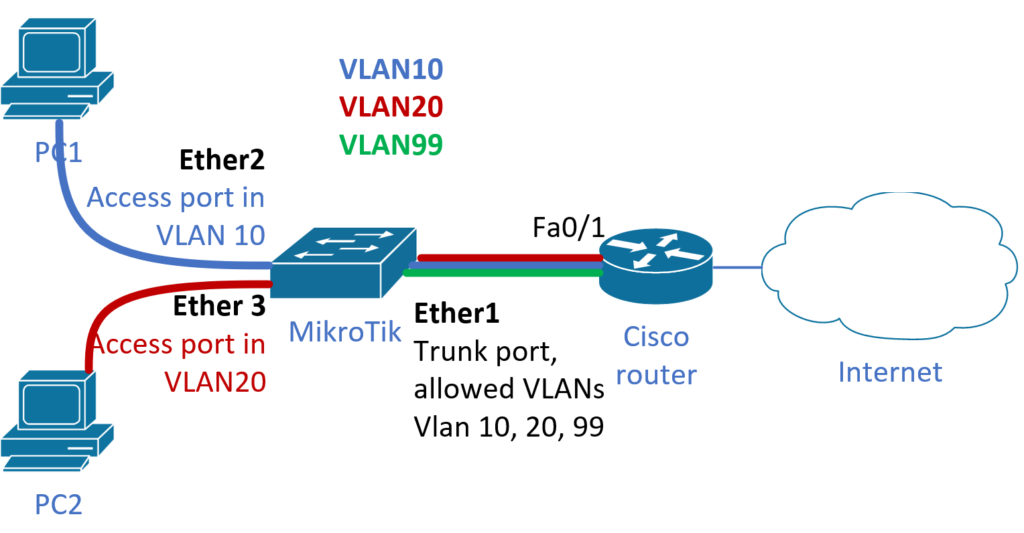
In this article, I will set up a simple LAN network consisting of two PCs, one Mikrotik box that acts as a L2 LAN switch, and one Cisco router that connects everything to the internet using NAT. PCs and Mikrotik switch are in the separate VirtualLANs (VLANs). My VLAN definition is:
- VLAN10, name Home, network address: 10.1.10.0/24, Mikrotik port: Ether 2
- VLAN20, name IoT, network address: 10.1.20.0/24, Mikrotik port: Ether 3
- VLAN99, name MGMT, network address: 10.1.99.0/24, Mikrotik port: bridge
- Ether port 1 will act as the trunk
Devices addresses:
- PC1, 10.1.10.2/24, def. gw. 10.1.10.1
- PC1, 10.1.20.2/24, def. gw. 10.1.20.1
- Mikrotik, 10.1.99.2/24, def. gw. 10.1.99.1
- Cisco router:
- VLA10: 10.1.10.1
- VLA20: 10.1.20.1
- VLA99: 10.1.99.1
Mikrotik resources
Mikrotik trunk and access port configuration links:
- Bridging and Switching: https://help.mikrotik.com/docs/display/ROS/Bridging+and+Switching
- VLANs: https://help.mikrotik.com/docs/display/ROS/VLAN
- Basic VLAN switching: https://help.mikrotik.com/docs/display/ROS/Basic+VLAN+switching
Note: Mikrotik devices in gns3 does not have built-in hw switch chip. Therefore the configuration is little bit different than on devices with built in chip.
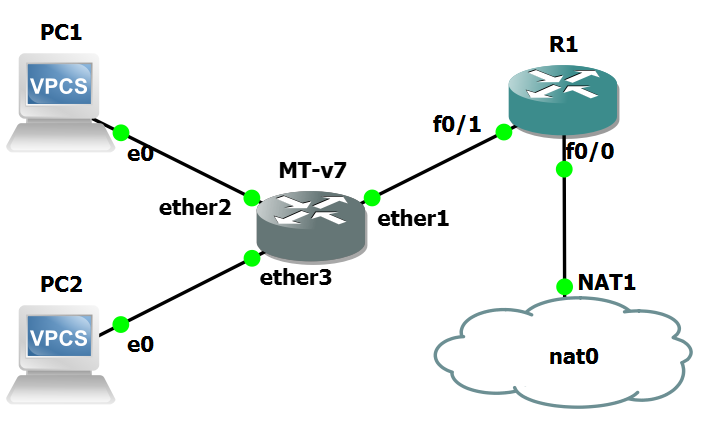
Topology
GNS3 topology
The R1 router config:
hostname R1
interface FastEthernet0/0
ip address dhcp
ip nat outside
no shut
interface FastEthernet0/1
no shut
interface FastEthernet0/1.10
encpapsulation dot1q 10
ip address 10.1.10.1 255.255.255.0
ip nat inside
interface FastEthernet0/1.20
encapsulation dot1q 20
ip address 10.1.20.1 255.255.255.0
ip nat inside
interface FastEthernet0/1.99
encapsulation dot1q 99
ip address 10.1.99.1 255.255.255.0
ip nat inside
ip access-list standard 1
permit 10.1.0.0 0.0.255.255
ip nat inside source list 1 int fa 0/0 overloadA test of connectivity
R1(config)#do ping 1.1.1.1 so fa 0/1.10
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
Packet sent with a source address of 10.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 8/16/40 ms
R1(config)#Networking on Mikrotik
As I’m focusing on the RouterOS configuration, here I will provide the RouterOS configuration In GNS3 the Mikrotik boot empty, and there is no configuration, no bridges and no port assignments.
First, we need to create the bridge
/interface bridge
add frame-types=admit-only-vlan-tagged name=main vlan-filtering=yes
Where
- frame-types specifies allowed ingress frame types on a bridge port. This property only has an effect when vlan-filtering is set to yes.
- name is the nameof the bridge
- vlan-filtering=yes .. enable VLAN functionality
To verify it type print
[admin@MikroTik] /interface/bridge> print
Flags: X - disabled, R - running
0 R name="main" mtu=auto actual-mtu=1500 l2mtu=65535 arp=enabled arp-timeout=auto
mac-address=0C:12:B3:7C:00:00 protocol-mode=rstp fast-forward=yes igmp-snooping=no
auto-mac=yes ageing-time=5m priority=0x8000 max-message-age=20s forward-delay=15s
transmit-hold-count=6 vlan-filtering=yes ether-type=0x8100 pvid=1
frame-types=admit-only-vlan-tagged ingress-filtering=yes dhcp-snooping=noNow we create VLANs
/interface vlan
add name=Home interface=main vlan-id=10
add name=IoT interface=main vlan-id=20
add name=MGMT interface=main vlan-id=99Verification
[admin@MikroTik] /interface/vlan> print
Flags: R - RUNNING
Columns: NAME, MTU, ARP, VLAN-ID, INTERFACE
# NAME MTU ARP VLAN-ID INTERFACE
0 R Home 1500 enabled 10 main
1 R IoT 1500 enabled 20 main
2 R MGMT 1500 enabled 99 main
Now we specify which kind of frames the port accepts or what it will do when will send frame out. Each bridge port have multiple VLAN related settings.
Ether1 as the trunk port accepts only tagged frames or in opposite, it send out frames properly tagged. Port ether 2 accept untagged frames which in ingress processing will be assigned to VLAN defined by pvid property. Or, port accept also frames tagged with correct VLAN ID (i.e. VLAN ID to which it belongs and which may also contain QoS Class of Service tag|) here it is VLAN ID 10 here. Similarly we configure ether 3 port for VLAN 20.
/interface bridge port
add bridge=main interface=ether1 frame-types=admit-only-vlan-tagged
add bridge=main interface=ether2 pvid=10 frame-types=admit-only-untagged-and-priority-tagged
add bridge=main interface=ether3 pvid=20 frame-types=admit-only-untagged-and-priority-taggedto verify type
admin@MikroTik] /interface/bridge/port> print
Columns: INTERFACE, BRIDGE, HW, PVID, PRIORITY, PATH-COST, INTERNAL-PATH-COST, HORIZON
# INTERFACE BRIDGE HW PVID PRIORITY PATH-COST INTERNAL-PATH-COST HORIZON
0 ether1 main yes 1 0x80 10 10 none
1 ether2 main yes 10 0x80 10 10 none
2 ether3 main yes 20 0x80 10 10 noneFinaly, we specify the trunk port processing. From the Mikrotik perspective we define, that ether1 port (that have defined frame-types=admit-only-vlan-tagged) in egress processing will set correct VLAN tag as is defined on tagged access ports.
/interface bridge vlan
add bridge=main tagged=ether1 vlan-ids=10
add bridge=main tagged=ether1 vlan-ids=20
add bridge=main tagged=ether1,main vlan-ids=99
Verification
admin@MikroTik] /interface/bridge/vlan> print
Columns: BRIDGE, VLAN-IDS
# BRIDGE VLAN-IDS
0 main 10
1 main 20
2 main 99Now we specify the IP address of the bridge to be able manage it over IP connection. This has nothing with VLANs and trunking.
/ip address
add address=10.1.99.2/24 interface=MGMTand finally add the default route
/ip route add dst-address=0.0.0.0/0 gateway=10.1.99.1
[admin@MikroTik] /ip/address> print
Columns: ADDRESS, NETWORK, INTERFACE
# ADDRESS NETWORK INTERFACE
0 10.1.99.2/24 10.1.99.0 MGMTFinal config should looks like
[admin@MikroTik] > export
# 2023-12-05 19:41:23 by RouterOS 7.12.1
# software id =
#
/interface bridge
add frame-types=admit-only-vlan-tagged name=main vlan-filtering=yes
/interface vlan
add interface=main name=Home vlan-id=10
add interface=main name=IoT vlan-id=20
add interface=main name=MGMT vlan-id=99
/interface bridge port
add bridge=main frame-types=admit-only-vlan-tagged interface=ether1
add bridge=main frame-types=admit-only-untagged-and-priority-tagged interface=ether2 \
pvid=10
add bridge=main frame-types=admit-only-untagged-and-priority-tagged interface=ether3 \
pvid=20
/interface bridge vlan
add bridge=main tagged=ether1 vlan-ids=10
add bridge=main tagged=ether1 vlan-ids=20
add bridge=main tagged=ether1,main vlan-ids=99
/ip address
add address=10.1.99.2/24 interface=MGMT network=10.1.99.0
/ip dhcp-client
# DHCP client can not run on slave or passthrough interface!
add interface=ether1
/ip route
add dst-address=0.0.0.0/0 gateway=10.1.99.1
/system note
set show-at-login=no
Final verification using ping
From PC1
PC1> ping 10.1.10.1
84 bytes from 10.1.10.1 icmp_seq=1 ttl=255 time=60.166 ms
84 bytes from 10.1.10.1 icmp_seq=2 ttl=255 time=16.222 ms
84 bytes from 10.1.10.1 icmp_seq=3 ttl=255 time=5.646 ms
^C
PC1> ping 1.1.1.1
84 bytes from 1.1.1.1 icmp_seq=1 ttl=50 time=20.098 ms
84 bytes from 1.1.1.1 icmp_seq=2 ttl=50 time=16.590 ms
84 bytes from 1.1.1.1 icmp_seq=3 ttl=50 time=15.860 ms
^C
PC1> ping 10.1.20.2
84 bytes from 10.1.20.2 icmp_seq=1 ttl=63 time=48.422 ms
84 bytes from 10.1.20.2 icmp_seq=2 ttl=63 time=16.633 ms
84 bytes from 10.1.20.2 icmp_seq=3 ttl=63 time=16.966 ms
^C
PC1> ping 10.1.99.1
84 bytes from 10.1.99.1 icmp_seq=1 ttl=255 time=6.143 ms
84 bytes from 10.1.99.1 icmp_seq=2 ttl=255 time=6.243 ms
^C
PC1> ping 10.1.99.2
84 bytes from 10.1.99.2 icmp_seq=1 ttl=63 time=19.523 ms
84 bytes from 10.1.99.2 icmp_seq=2 ttl=63 time=16.822 ms
84 bytes from 10.1.99.2 icmp_seq=3 ttl=63 time=16.655 ms
^C
