In this article I'm just testing guides available at the cisco support forum (the same guide at the cisco site) or very good guide at L2TP/IPSec with Windows 8/7 and Cisco ASA 8.x/9.x, as I need a secure access to my academys network. For years I had used native Cisco vpn client (not longer supported), and then on win 10 the shresoft vpn client. Both of them are not available for android devices (tablets, smart phones). Ido not use Anyconnect, as it is licensed. I'm expecting to run previously defined IPsec client based VPN together with clientless L2TP over IPSec VPN.
Prerequisities:
- an L2TP client (built into an android device or windows)
- ASA firewal with system image of the version 8.2.5 or later. Check the version with :
kis-asa-5515X# sh version | in image System image file is "disk0:/asa861-2-smp-k8.bin"
- AAA and an adress pool
- IKEv1 phase 1 – using 3DES encryption with SHA1 hash method and pre shared key
- IPsec phase 2 – using 3DES or AES encryption with MD5 or SHA hash method.
- Group policy, tunnel group and PPP Authentication (only PAP, MS-CHAPv1, or MSCHAPv2 (preferred) are supported).
Configuration
1. AAA and an IP address pool
1. To allocate IP addresses to the L2TP clients we may use a predefined addess pool (my case), or define a new local address pool, or use a dhcp-server for the adaptive security appliance.
So, in my case there is an existing one:
kis-asa-5515X# sh run | in local pool ip local pool KIS-VPN-POOL 10.0.0.15-10.0.0.254 mask 255.255.255.0
ip local pool pool_name starting_address-ending_address mask subnet_mask
whose example may look like:
hostname(config)# ip local pool KIS_L2TP_POOL 10.0.255.15-10.0.255.254 mask 255.255.255.0
2. Create a local account (for example for testing puposes, then another AAA mechanims may be configured)
! username NAME password PASS msachp conf t username skuska password **** msachp
NOTE: the command has to end with the mschap attribute, using just username with password does not work!
Check:
kis-asa-5515X# sh run | in skuska
username skuska password alNPeMUMkMOIVnhVVPUvlQ== nt-encrypted
2. Configuring IKEv1
3. define IKEv1 using preshared key, 3des (tested) or aes (not tested) encryption, hashing mechanism, diffie-hellman group and parameter lifetime:
crypto ikev1 policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
4. enable ISAKMP (IKEv1) on the ASA outside interface
crypto ikev1 enable outside
Check:
kis-asa-5515X# sh run crypto ikev1 crypto ikev1 enable outside ! my client based IPsec crypto ikev1 policy 1 authentication pre-share encryption aes-256 hash sha group 2 lifetime 3600 ! work for L2TP crypto ikev1 policy 10 authentication pre-share encryption 3des hash sha group 2 lifetime 86400
3. Configuring IPsec
5. Next we create a transform set with specific ESP encryption and hashing type
! crypto ipsec ikev1 transform-set NAME esp-3des esp-sha-hmac
!
! in my case
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
and we instruct IPsec to use transport mode (required) rather than tunnel mode.
! crypto ipsec ikev1 transform-set NAME mode transport ! ! in my case crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
6. alternatively we may create several transform sets, for example
crypto ipsec transform-set ESP-AES-SHA-TRANS esp-aes esp-sha-hmac crypto ipsec transform-set ESP-AES-SHA-TRANS mode transport
Check:
kis-asa-5515X# sh run crypto ipsec crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-SHA-TRANS esp-aes esp-sha-hmac crypto ipsec ikev1 transform-set ESP-AES-SHA-TRANS mode transport
7. Now we will create a a dynamic crypto map, which is using specified transfom sets (max 7) and then we map it to an ordinary crypto map. This feature is not documented within of the Configuring L2TP over IPSec guide.
So, create a dynamic map with specified name using defined transform sets:
! crypto dynamic-map NAME 10 set ikev1 transform-set YOUR-TRANSFORM-SET1 TRANSFORM-SET2 ... ! ! in my case crypto dynamic-map L2TP-VPN-DYN-MAP 10 set ikev1 transform-set ESP-3DES-SHA-TRANS ESP-AES-SHA-TRANS
and attach the dynamic map to a crypto map
! crypto map vpn 20 ipsec-isakmp dynamic dyno ! ! in my case crypto map L2TP-VPN 10 ipsec-isakmp dynamic L2TP-VPN-DYN-MAP
Check
kis-asa-5515X# sh run crypto dynamic-map crypto dynamic-map L2TP-VPN-DYN-MAP 10 set ikev1 transform-set ESP-3DES-SHA-TRANS ESP-AES-SHA-TRANS
8. apply the crypto map on the outside interface
crypto map L2TP-VPN interface outside
Check:
kis-asa-5515X# sh run crypto map crypto map L2TP-VPN 10 ipsec-isakmp dynamic L2TP-VPN-DYN-MAP crypto map L2TP-VPN interface outside
NOTE: If your ASA is already using some crypto map (for legacy IPsecVPN for example), you can not apply more as one crypto map per interface (commands overwrite each other).
Therefore you need to modify an existing dynamic crypto map and extend used transform sets with a new one, but used for the L2TP tunnel. We can not just add a new crypto map line to an existing dynamic crypto map.
For example I already had configured an ordinary IPsec crypto map
crypto map KIS-VPN-MAP 1 ipsec-isakmp dynamic KIS-VPN-DYN-MAP
which is linked with already defined IPSec dynamic crypto map
crypto dynamic-map KIS-VPN-DYN-MAP 1 set ikev1 transform-set ESP-AES-256-SHA
adding just another line
crypto dynamic-map KIS-VPN-DYN-MAP 10 set ikev1 transform-set ESP-3DES-SHA-TRANS ESP-AES-SHA-TRANS
does not work!!! The VPN establishment process ends with QM FSM error and Phase 2 mismatch error (see thsoot section at the bottom).
We need to extend the DYNAMIC crypto map configuration with all supported transform sets:
Previous:
crypto dynamic-map KIS-VPN-DYN-MAP 1 set ikev1 transform-set ESP-AES-256-SHA
TO the same but extended:
crypto dynamic-map KIS-VPN-DYN-MAP 1 set ikev1 transform-set ESP-AES-256-SHA ESP-3DES-SHA-TRANS ESP-AES-SHA-TRANS
4. Configuring group policy and tunnel groups (profiles)
9. Create an internal group-policy (or we may use a “DfltGrpPolicy” default policy)
! command:
! group-policy NAME internal
!
! which for my case is:
group-policy L2TP_IPSEC_POLICY internal
and specify policy attributes:
- where we specifies L2TP/IPsec as the vpn tunneling protocol.
- and we instruct ASA to assign DNS server IP address to a client for the group policy.
! command:
! group-policy NAME attributes
dns-server value <dns_server>
vpn-tunnel-protocol l2tp-ipsec
!
! which for my case is:
group-policy L2TP_IPSEC_POLICY attributes
dns-server value 158.193.152.2
vpn-tunnel-protocol l2tp-ipsec
10. Now we may either to create a new connection profile (tunnel group) (works with limitations) or just to modify the attributes of the existing DefaultRAGroup (works without problems). Then we define general-attributes of the tunnel group that will be used.
- Map defined group policy to the tunnel group
- Map defined address pool to be used by this connection profile (tunnel group)
- Optionally specifies a method to authenticate users attempting L2TP over IPsec connections, for the connection profile (tunnel group). If we are not using the ASA to perform local authentication, add fallback to local authentication specifying LOCAL to the end of the command.
! !! modify default profile ! ! tunnel-group DefaultRAGroup general-attributes ! default-group-policy OUR_POLICY ! address-pool OUR_ADDRESS_POOL ! authentication-server-group NAME_OF_AAA_SOURCES LOCAL ! ! or create a new one ! ! tunnel-group NAME_OF_NEW_TUNNEL_GROUP_PROFILE type remote-access ! ! tunnel-group NAME_OF_NEW_TUNNEL_GROUP_PROFILE general-attributes ! default-group-policy OUR_POLICY ! address-pool OUR_ADDRESS_POOL ! ! for my case i've tiredto create a new tunnel group for l2tp only ! tunnel-group KIS_L2TP_PROFILE type remote-access tunnel-group KIS_L2TP_PROFILE general-attributes default-group-policy L2TP_IPSEC_POLICY address-pool KIS_L2TP_POOL
Important Note: after some testing I need to mention, that using own profile (tunnel-group) is a problem. Using win 10 build in l2tp client there is no possibility to setup and define tunnel group name (profile). Than on my ASA box I have received following error messages:
kis-asa-5515X# debug crypto ikev1
kis-asa-5515X# Mar 01 20:06:14 [IKEv1]Group = 37.61.161.245, IP = 37.61.161.245,Can't find a valid tunnel group, aborting...!
Mar 01 20:06:15 [IKEv1]IP = 37.61.161.245, Header invalid, missing SA payload! (next payload = 4)
...
"If we authenticate devices with pre-shared keys, we must use “DefaultRAGroup” tunnel group"
tunnel-group DefaultRAGroup general-attributes
default-group-policy L2TP_IPSEC_POLICY
address-pool KIS-VPN-POOL
tunnel-group DefaultRAGroup ipsec-attributes
ikev1 pre-shared-key ******
11. Now we specify the PPP authentication protocol for the tunnel group. Don't forgett that for PPP authentication only PAP, MS-CHAPv1, or MS-CHAPv2 (preferred) are supported
! hostname(config)# tunnel-group NAME_OF_NEW_TUNNEL_GROUP_PROFILE ppp-attributes ! hostname(config-ppp)# authentication ms-chap-v1 ! ! in my case tunnel-group KIS_L2TP_PROFILE ppp-attributes no authentication pap no authentication chap no authentication ms-chap-v1 authentication ms-chap-v2
12.Now we will define the pre-shared key for our tunnel group (connection profile)
! tunnel-group DefaultRAGroup ipsec-attributes
! pre-shared-key *
!
!
! in my case
tunnel-group KIS_L2TP_PROFILE ipsec-attributes
ikev1 pre-shared-key ****PASSWORD****
Checking the PSK key:
more system:running-config | in shared
Final configuration
Here is working final configuration gathered from previous steps, that look like:
! account for a local authentication
username skuska password **** mschap
! pool of addresses used to assing to l2tp cliets
ip local pool KIS_L2TP_VPN_POOL 10.0.255.1-10.0.255.254 mask 255.255.255.0
! ikev1
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
! IPsec
! one transform set
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
!another TS
crypto ipsec transform-set ESP-AES-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec transform-set ESP-AES-SHA-TRANS mode transport
! dynamic crypto map
crypto dynamic-map L2TP-VPN-DYN-MAP 10 set ikev1 transform-set ESP-3DES-SHA-TRANS ESP-AES-SHA-TRANS
! mapping dynamic crypto map to a crypto map
crypto map L2TP-VPN 10 ipsec-isakmp dynamic L2TP-VPN-DYN-MAP
! applying crypto map to the interface
crypto map L2TP-VPN interface outside
! l2tp policy
group-policy L2TP_IPSEC_POLICY internal
group-policy L2TP_IPSEC_POLICY attributes
dns-server value 158.193.152.2
vpn-tunnel-protocol l2tp-ipsec
! modifying default tunnel profile
tunnel-group DefaultRAGroup general-attributes
default-group-policy L2TP_IPSEC_POLICY
address-pool KIS-VPN-POOL
! ppp attrib
tunnel-group DefaultRAGroup ppp-attributes
no authentication pap
no authentication chap
no authentication ms-chap-v1
authentication ms-chap-v2
tunnel-group DefaultRAGroup ipsec-attributes
ikev1 pre-shared-key ***
5. AAA authentication
Here described configuration is using for authentication purposes LOCAL database of accounts. I'm using central MS Active directory controller for that. Now i will just add a small configuration how to authenticate users of L2TP VPN against MS AD. The AD service of course have to run within your network.
5.1 define AAA server
! aaa-server NAME protocol radius ! aaa-server NAME (interface) host IP ADDRESS ! key ***** ! ! which is in my case aaa-server KIS-PDC protocol radius aaa-server KIS-PDC (vlan10) host 192.168.10.2 key *****
5.2 Modify tunnel group general parameters to add AAA server
Here is used config
tunnel-group DefaultRAGroup general-attributes
default-group-policy L2TP_IPSEC_POLICY
address-pool KIS-VPN-POOL
which is extended with
authentication-server-group KIS-PDC
final block look like:
tunnel-group DefaultRAGroup general-attributes
default-group-policy L2TP_IPSEC_POLICY
address-pool KIS-VPN-POOL
authentication-server-group KIS-PDC
NAT and ACL
Do not forgett to solve the NAT and ACL!
Setting a L2TP client
Configuring Android 5.0.2, core 3.4.0+
- Open the menu and choose Settings
- Select Tethering and Netowrks
- Select VPN
- Select Add VPN
- Then set VPN name, VPN type (L2TP/IPSec PSK), Server IP address and set IPSec pre-shared key (password)
- Do not set L2TP secret
- Open the menu and choose Save
- Then Select just created VPN
- Set user name nad password
- Check Save account information
- click on Connect …Done
Win10
Nice tutorial with images is available at https://www.cactusvpn.com/tutorials/how-to-set-up-l2tp-vpn-on-windows-10/
So:
- Open "Network and Sharing center",
- Select "Set up a new connection or network"
- Select "Connect to a workplace", click "Next", select "Use my Internet connection (VPN)", then
- Set ASA's IP address into a Internet address form and select descriptive name to a "Destination name" form, and click create.
- Once created go back to "Network and Sharing center", and from left menu select "Change adapter settings", you should see all your network adapters, among them your just created L2TP VPN adapter, you may notice that under adapter name is written IKEv2. So we need to modify the settings.
- Right click on l2tp adapter, select "Properties", choose "Security" tabs and there set correct "Type of VPN" to L2TP/IPsec
- Then click on "Advanced settings" under of "Types of VPN", where you should setup your pre-shared key.
- Click on "Ok" and you will go back to Adapter properties window.
- As "Data enccyption" choose "Maximal strenght …"
- within "Authentication" select "Allow these protocols" and select Microsoft CHAP v2 (ms-chap-v2). Click on Yes.
- Now make a right click on the L2TP adapter and select Connect, and then again Connect.
- System will prompt you for Username and Password
Verification and tshooting
Use these commands to confirm that your connection works properly.
- terminal monitor (see debuging info on your vty session)
- show run crypto ikev1(8.3.2.12+)
- show run crypto dynamic-map
- show run crypto ipsec
- show vpn-sessiondb ra-ikev1-ipsec (8.3.2.12+)
- show vpn-sessiondb remote (8.2.5)
- debug crypto ikev1
- more system:running-config | in shared
- sh crypto ipsec sa (see connected users)
Tshooting of observed problems
Some of problem solving I had already mentioned. Just repeat:
Own tunnel-group problem
Debug output similar for both L2tp clients trying to access (Android, Win)
kis-asa-5515X# Feb 29 20:40:54 [IKEv1]Group = 37.61.161.245, IP = 37.61.161.245, Can't find a valid tunnel group, aborting...!
Feb 29 20:40:57 [IKEv1]IP = 37.61.161.245, Header invalid, missing SA payload! (next payload = 4)
Feb 29 20:40:59 [IKEv1]IP = 37.61.161.245, Header invalid, missing SA payload! (next payload = 4)
Bad IPsec Password
Once you make a mistype on your password you may receive following message:
kis-asa-5515X# Mar 01 20:36:46 [IKEv1]Group = DefaultRAGroup, IP = 37.61.161.245, Received encrypted Oakley Main Mode packet with invalid payloads, MessID = 0
Mar 01 20:36:46 [IKEv1]Group = DefaultL2LGroup, IP = 37.61.161.245, ERROR, had problems decrypting packet, probably due to mismatched pre-shared key. Aborting
QM FSM Error
Running debug crypto ikev1 we may observe the message:
kis-asa-5515X# Mar 01 22:06:08 [IKEv1]Group = DefaultRAGroup, IP = 37.61.161.245, QM FSM error
(P2 struct &0x00007fff2ef9bf50, mess id 0x1)!
Mar 01 22:06:08 [IKEv1]Group = DefaultRAGroup, IP = 37.61.161.245, Removing peer from correlator
table failed, no match!
Mar 01 22:06:08 [IKEv1]Group = DefaultRAGroup, IP = 37.61.161.245, Session is being torn down.
Reason: Phase 2 Mismatch
Possible reason is mismatching of the transform set parameters.
Bad PPP name / password
Windows print
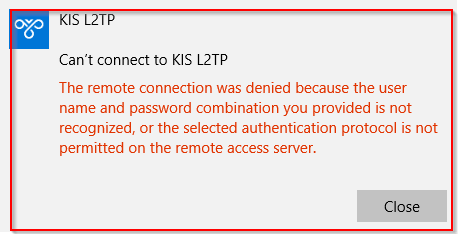
which means:
1) windows side: bad combination of username and password
2) on asa side: local account created without using mschap attribute
Helpfull links
- Cisco ASA 5500 Series Configuration Guide using the CLI, 8.4 and 8.6: Configuring L2TP over IPsec
- Cisco ASA 5500 Series Configuration Guide using the CLI, 8.3: Information about NAT
- IPsec Troubleshooting: Understanding and Using debug Commands
