This config example shows a Site-to-Site configuration of IPsec VPN established between two Cisco routers. VPN will use IKEv2 protocol with PreSharedKey (PSK) remote-site authentication. Topology simulates a Branch router connected over an ISP to the HQ router. There are several options for how to configure IKEv2. In this example, I’m using the symmetric PSK witch crypto map, where the IKEv2 process is started by ACL that identifies interesting traffic. I also do not use GRE tunnel for the interconnection of both sides, instead, simple static default routes are used.
Topology
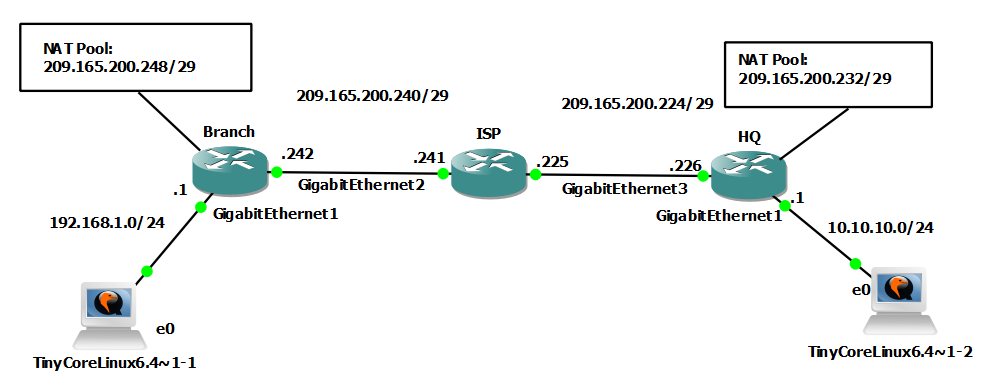
Configuration runs on GNS3 emulator and I’m using the CSR1000v platform with version 16.12.01a IOS XE as the older ISR platform (7200 15.4 IOS) does not support IKEv2. On real devices, IKEv2 is supported on Cisco ISR Generation 2 (G2) that runs Cisco IOS software version 15.2(4)M or later (for example 29xx ISR), ASA with 8.4.(1) and later (including ASA 5510).
Note: I use TinyLinux endpoints to generate traffic of interest from LAN to LAN because the advanced ping command on Branch and HE did not work well and did not start the IKEv2 processing.
Initial configuration
Initial configuration includes:
- the setting of basic IP addressing, NAT, DHCP pools and specifying static routes.
| Branch | ISP | HQ |
| ena conf t hostname BRANCH int g1 ip add 192.168.1.1 255.255.255.0 ip nat inside no shut int g2 ip add 209.165.200.242 255.255.255.248 ip nat outside no shu exit ip access-list extended NAT 10 deny ip 192.168.1.0 0.0.0.255 10.10.10.0 0.0.0.255 log 20 permit ip 192.168.1.0 0.0.0.255 any log ip nat inside source list NAT int g2 overload ip route 0.0.0.0 0.0.0.0 g2 209.165.200.241 ip dhcp pool LAN network 192.168.1.0 /24 default-router 192.168.1.1 line con 0 logging synchronous end wr mem | ena conf t hostname ISP int g2 ip add 209.165.200.241 255.255.255.248 no shut int g3 ip add 209.165.200.225 255.255.255.248 no shu exit Line con 0 logging synchronous end wr mem | ena conf t hostname HQ int g1 ip add 10.10.10.1 255.255.255.0 ip nat inside no shut int g3 ip add 209.165.200.226 255.255.255.248 ip nat outside no shu exit ip access-list extended NAT 10 deny ip 10.10.10.0 0.0.0.255 192.168.1.0 0.0.0.255 log 20 permit ip 10.10.10.0 0.0.0.255 any log ip nat inside source list NAT int g3 overload ip route 0.0.0.0 0.0.0.0 g3 209.165.200.225 ip dhcp pool LAN_HQ network 10.10.10.0 /24 default-router 10.10.10.1 Line con 0 logging synchronous end wr mem |
Configuration of IPsec VPN with IKEv2 and PSK authentication
To perform this task we need to configure IPsec main components that include:
- IKEv2 Proposal
- IKEv2 Policy
- IKEv2 Profile
- IKEv2 Keyring
- IPsec transform set
- and Crypto Map (the other option is to define IPSec profile and applly it on a GRE tunnel)
Configuring IKEv2 keyring
An IKEv2 keyring is a repository of symmetric and asymmetric preshared keys and is independent of the IKEv1 key ring. The IKEv2 keyring is associated with an IKEv2 profile and hence supports a set of peers that match the IKEv2 profile. The IKEv2 key ring gets its VPN routing and forwarding (VRF) context from the associated IKEv2 profile.
To configure type :
crypto ikev2 keyring NAME _OF_KEYRING
peer NAME_OF_PEER
address IP_ADDRES_OF_NEIGHBOR
pre-shared-key PASSWORD
In my case, I’m using the symmetric preshared key for both sites. But even asymmetric may be used
crypto ikev2 keyring NAME _OF_KEYRING
peer NAME_OF_PEER
address IP_ADDRES_OF_NEIGHBOR
pre-shared-key local PASSWORD_1
pre-shared-key remote PASSWORD_2
The configuration for my Branch router:
BRANCH(config)#crypto ikev2 keyring KEYRING_1 ! thare can be several peers identified several ways, i'm using peer IP address BRANCH(config-ikev2-keyring)# peer HQ_ROUTER BRANCH(config-ikev2-keyring-peer)# address 209.165.200.226 BRANCH(config-ikev2-keyring-peer)# pre-shared-key MY_PASS_cisco123
and for HQ:
HQ(config)# crypto ikev2 keyring KEYRING_1 HQ(config-ikev2-keyring)# peer BRANCH_ROUTER HQ(config-ikev2-keyring-peer)# address 209.165.200.242 HQ(config-ikev2-keyring-peer)# pre-shared-key MY_PASS_cisco123
Configuring IKEv2 proposal
KEv2 proposal is a collection of transforms used in the negotiation of Internet Key Exchange (IKE) security associations (SAs) as part of the IKE_SA_INIT exchange. The transform types used in the negotiation are as follows:
- Encryption algorithm
- Integrity algorithm
- Pseudo-Random Function (PRF) algorithm
- Diffie-Hellman (DH) group
Be careful to configure recommended methods, for example, one of them is the aes-gcm encryption and prf integrity methods.
To configure the proposal type
!proposal crypto ikev2 proposal NAME_OF_PROPSOAL encryption TYPE prf TYPE group GROUP
or specifically for my Branch
!proposal BRANCH(config)#crypto ikev2 proposal MY_IKEV2_PROPOSAL IKEv2 proposal MUST either have a set of an encryption algorithm other than aes-gcm, an integrity algorithm and a DH group configured or encryption algorithm aes-gcm, a prf algorithm and a DH group configured BRANCH(config-ikev2-proposal)#encryption aes-gcm-256 BRANCH(config-ikev2-proposal)#prf sha512 BRANCH(config-ikev2-proposal)#group 21
and the same for the HQ
HQ(config)#crypto ikev2 proposal MY_IKEV2_PROPOSAL
IKEv2 proposal MUST either have a set of an encryption algorithm other than aes-gcm, an integrity algorithm and a DH group configured or
encryption algorithm aes-gcm, a prf algorithm and a DH group configured
HQ(config-ikev2-proposal)#encryption aes-gcm-256
HQ(config-ikev2-proposal)#prf sha512
HQ(config-ikev2-proposal)#group 21
IKEv2 Policy
An IKEv2 policy contains proposals that are used to negotiate the encryption, integrity, PRF algorithms, and DH group in the IKE_SA_INIT exchange. It can have match statements, which are used as selection criteria to select a policy during negotiation.
The policy is configured by typing
!policy crypto ikev2 policy POLICY_NAME proposal PROPOSAL_NAME
For the Branch router:
BRANCH(config)#crypto ikev2 policy BRANQ_TO_HQ_POLICY IKEv2 policy MUST have atleast one complete proposal attached BRANCH(config-ikev2-policy)#proposal MY_IKEV2_PROPOSAL
For HQ
HQ(config)#crypto ikev2 policy HQ_TO_BRANCH_POLICY IKEv2 policy MUST have atleast one complete proposal attached HQ(config-ikev2-policy)# proposal MY_IKEV2_PROPOSAL
Configuring IKEv2 Profile
An IKEv2 profile is a repository of nonnegotiable parameters of the IKE SA, such as local or remote identities and authentication methods and services that are available to authenticated peers that match the profile. An IKEv2 profile must be attached to either a crypto map or an IPSec profile on the initiator. An IKEv2 profile is not mandatory on the responder.
In my case, I’m using the IP address as the identity of my peers.
For the Branch
BRANCH(config)#crypto ikev2 profile IKE_BRANCH_TO_HQ_PROFILE IKEv2 profile MUST have: 1. A local and a remote authentication method. 2. A match identity or a match certificate or match any statement. BRANCH(config-ikev2-profile)#match address local 209.165.200.242 BRANCH(config-ikev2-profile)# match identity remote address 209.165.200.226 255.255.255.248 BRANCH(config-ikev2-profile)#authentication local pre-share BRANCH(config-ikev2-profile)#authentication remote pre-share BRANCH(config-ikev2-profile)#keyring local KEYRING_1
For HQ:
HQ(config)#crypto ikev2 profile IKE_HQ_TO_BRANCH_PROFILE IKEv2 profile MUST have: 1. A local and a remote authentication method. 2. A match identity or a match certificate or match any statement. HQ(config-ikev2-profile)# match address local 209.165.200.226 HQ(config-ikev2-profile)# match identity remote address 209.165.200.242 255.255.255.248 HQ(config-ikev2-profile)# authentication remote pre-share HQ(config-ikev2-profile)# authentication local pre-share HQ(config-ikev2-profile)# keyring local KEYRING_1
IPsec transform set
A Transform Set is used to define how the data traffic between IPSec peers is going to be operated and protected.
On my Branch
BRANCH(config)#crypto ipsec transform-set IPSEC_TR_SET esp-aes 256 BRANCH(cfg-crypto-trans)#mode tunnel
On HQ
HQ(config)#crypto ipsec transform-set IPSEC_TR_SET esp-aes 256 HQ(cfg-crypto-trans)# mode tunnel HQ(cfg-crypto-trans)#exit
ACL
Crypto ACL is just an ACL created to identify interesting traffic that starts the IPsec tunnel initialization.
Branch
ip access-list extended ACL remark Preotect flows form Branch to HQ permit ip 192.168.1.0 0.0.0.255 10.10.10.0 0.0.0.255
HQ
ip access-list extended ACL remark Preotect flows form HQ to Branch permit ip 10.10.10.0 0.0.0.255 192.168.1.0 0.0.0.255
Crypto Map
Crypto Maps are used to connect all the pieces of IPSec configuration together. A Crypto Map consists of one or more entries as an ACL, Transform Set, Remote Peer, the lifetime of the data connections etc
Branch
BRANCH(config)#crypto map MY_MAP 10 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
BRANCH(config-crypto-map)# set peer 209.165.200.226
BRANCH(config-crypto-map)# set transform-set IPSEC_TR_SET
BRANCH(config-crypto-map)# set ikev2-profile IKE_BRANCH_TO_HQ_PROFILE
BRANCH(config-crypto-map)# match address ACL
HQ
HQ(config-if)#crypto map MY_MAP 10 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
HQ(config-crypto-map)# set peer 209.165.200.242
HQ(config-crypto-map)# set transform-set IPSEC_TR_SET
HQ(config-crypto-map)# set ikev2-profile IKE_HQ_TO_BRANCH_PROFILE
HQ(config-crypto-map)# match address ACL
Applying the Crypto map
Crypto m,ap must be applied on ongoing interface
Branch
interface g2 crypto map MY_MAP
HQ
interface g3 crypto map MY_MAP
Verification – generating interesting traffic
Ping from one PC to another. I’ve used this as the advanced ping from Branch/HQ routers did not work
gns3@box:~$ ping 10.10.10.1
PING 10.10.10.1 (10.10.10.1): 56 data bytes
64 bytes from 10.10.10.1: seq=0 ttl=254 time=60.096 ms
64 bytes from 10.10.10.1: seq=1 ttl=254 time=9.588 ms
64 bytes from 10.10.10.1: seq=2 ttl=254 time=4.655 ms
64 bytes from 10.10.10.1: seq=3 ttl=254 time=4.118 ms
^C
--- 10.10.10.1 ping statistics ---
4 packets transmitted, 4 packets received, 0% packet loss
round-trip min/avg/max = 4.118/19.614/60.096 ms
gns3@box:~$
and opposite
gns3@box:~$ ping 192.168.1.1
PING 192.168.1.1 (192.168.1.1): 56 data bytes
64 bytes from 192.168.1.1: seq=0 ttl=254 time=20.755 ms
64 bytes from 192.168.1.1: seq=1 ttl=254 time=6.157 ms
^C
--- 192.168.1.1 ping statistics ---
2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max = 6.157/13.456/20.755 ms
gns3@box:~$
Verification – show commands
focus on IKEv2
BRANCH#sh crypto ikev2 ? authorization Author policy certificate-cache Show certificates in ikev2 certificate-cache client Show Client Status cluster Show Cluster load diagnose Shows ikev2 diagnostic policy Show policies profile Shows ikev2 profiles proposal Show proposals sa Shows ikev2 SAs session Shows ikev2 active session stats Shows ikev2 sa stats
Focus on IPsec
BRANCH#sh crypto ipsec ? out-sa-hash IPsec Outbound SA Hash for VESEN policy Show IPSEC client policies profile Show ipsec profile information sa IPSEC SA table security-association Show parameters for IPSec security associations spi-lookup IPSEC SPI table transform-set Crypto transform sets
Info on sessions
BRANCH#sh crypto session ? active Shows HA-enabled crypto sessions in the active state brief brief output detail detailed output fvrf Front-door VRF groups show all connected groups usage interface Show crypto sessions on the interface isakmp Show crypto sessions using the isakmp profile or group ivrf Inside VRF local Show crypto sessions for a local crypto endpoint remote Show crypto sessions for a remote IKE peer standby Shows HA-enabled crypto sessions in the standby state summary show groups and their members username Show crypto session for xauth or pki-aaa username | Output modifiers
and we must see one session as UP and ACTIVE
BRANCH#sh crypto session detail
Crypto session current status
Code: C - IKE Configuration mode, D - Dead Peer Detection
K - Keepalives, N - NAT-traversal, T - cTCP encapsulation
X - IKE Extended Authentication, F - IKE Fragmentation
R - IKE Auto Reconnect, U - IKE Dynamic Route Update
S - SIP VPN
Interface: GigabitEthernet2
Profile: IKE_BRANCH_TO_HQ_PROFILE
Uptime: 00:37:20
Session status: UP-ACTIVE
Peer: 209.165.200.226 port 500 fvrf: (none) ivrf: (none)
Phase1_id: 209.165.200.226
Desc: (none)
Session ID: 1
IKEv2 SA: local 209.165.200.242/500 remote 209.165.200.226/500 Active
Capabilities:U connid:1 lifetime:23:22:40
IPSEC FLOW: permit ip 192.168.1.0/255.255.255.0 10.10.10.0/255.255.255.0
Active SAs: 2, origin: crypto map
Inbound: #pkts dec'ed 40 drop 0 life (KB/Sec) 4607995/1362
Outbound: #pkts enc'ed 40 drop 0 life (KB/Sec) 4607996/1362
Debugging
Sources
IOS IKEv2 Debugs for Site-to-Site VPN with PSKs Troubleshooting TechNote
Debug command
debug crypto ikev2 packet
debug crypto ikev2 internal
and one captured during the IPsec initialization:
BRANCH# *Nov 24 07:57:56.722: %SEC-6-IPACCESSLOGDP: list ACL permitted icmp 192.168.1.2 -> 10.10.10.1 (8/0), 1 packet *Nov 24 07:57:56.735: IKEv2:% Getting preshared key from profile keyring KEYRING_1 *Nov 24 07:57:56.736: IKEv2:% Matched peer block 'HQ_ROUTER' *Nov 24 07:57:56.738: IKEv2:(SESSION ID = 0,SA ID = 0):Searching Policy with fvrf 0, local address 209.165.200.242 *Nov 24 07:57:56.738: IKEv2:(SESSION ID = 0,SA ID = 0):Found Policy 'BRANQ_TO_HQ_POLICY' *Nov 24 07:57:56.743: IKEv2:(SESSION ID = 1,SA ID = 1):[IKEv2 -> Crypto Engine] Computing DH public key, DH Group 21 *Nov 24 07:57:56.757: IKEv2:(SESSION ID = 1,SA ID = 1):(SA ID = 1):[Crypto Engine -> IKEv2] DH key Computation PASSED *Nov 24 07:57:56.757: IKEv2:(SESSION ID = 1,SA ID = 1):Request queued for computation of DH key *Nov 24 07:57:56.759: IKEv2:(SESSION ID = 1,SA ID = 1):IKEv2 initiator - no config data to send in IKE_SA_INIT exch *Nov 24 07:57:56.759: IKEv2:(SESSION ID = 1,SA ID = 1):Generating IKE_SA_INIT message *Nov 24 07:57:56.760: IKEv2:(SESSION ID = 1,SA ID = 1):IKE Proposal: 1, SPI size: 0 (initial negotiation), Num. transforms: 3 AES-GCM SHA512 DH_GROUP_521_ECP/Group 21 *Nov 24 07:57:56.764: IKEv2:(SESSION ID = 1,SA ID = 1):Sending Packet [To 209.165.200.226:500/From 209.165.200.242:500/VRF i0:f0] Initiator SPI : 2BD7494C28C698F0 - Responder SPI : 0000000000000000 Message id: 0 IKEv2 IKE_SA_INIT Exchange REQUEST Payload contents: SA KE N VID VID VID VID NOTIFY(NAT_DETECTION_SOURCE_IP) NOTIFY(NAT_DETECTION_DESTINATION_IP) *Nov 24 07:57:56.767: IKEv2:(SESSION ID = 1,SA ID = 1):Insert SA *Nov 24 07:57:56.943: IKEv2:(SESSION ID = 1,SA ID = 1):Received Packet [From 209.165.200.226:500/To 209.165.200.242:500/VRF i0:f0] Initiator SPI : 2BD7494C28C698F0 - Responder SPI : 3B5D666A9F360298 Message id: 0 IKEv2 IKE_SA_INIT Exchange RESPONSE Payload contents: SA KE N VID VID VID VID NOTIFY(NAT_DETECTION_SOURCE_IP) NOTIFY(NAT_DETECTION_DESTINATION_IP) CERTREQ NOTIFY(HTTP_CERT_LOOKUP_SUPPORTED) *Nov 24 07:57:56.947: IKEv2:(SESSION ID = 1,SA ID = 1):Processing IKE_SA_INIT message *Nov 24 07:57:56.947: IKEv2:(SESSION ID = 1,SA ID = 1):Verify SA init message *Nov 24 07:57:56.947: IKEv2:(SESSION ID = 1,SA ID = 1):Processing IKE_SA_INIT message *Nov 24 07:57:56.947: IKEv2:(SESSION ID = 1,SA ID = 1):Checking NAT discovery *Nov 24 07:57:56.947: IKEv2:(SESSION ID = 1,SA ID = 1):NAT not found *Nov 24 07:57:56.948: IKEv2:(SESSION ID = 1,SA ID = 1):[IKEv2 -> Crypto Engine] Computing DH secret key, DH Group 21 *Nov 24 07:57:56.985: IKEv2:(SESSION ID = 1,SA ID = 1):(SA ID = 1):[Crypto Engine -> IKEv2] DH key Computation PASSED *Nov 24 07:57:56.985: IKEv2:(SESSION ID = 1,SA ID = 1):Request queued for computation of DH secret *Nov 24 07:57:56.986: IKEv2:(SESSION ID = 1,SA ID = 1):(SA ID = 1):[IKEv2 -> Crypto Engine] Calculate SKEYSEED and create rekeyed IKEv2 SA *Nov 24 07:57:56.989: IKEv2:(SESSION ID = 1,SA ID = 1):(SA ID = 1):[Crypto Engine -> IKEv2] SKEYSEED calculation and creation of rekeyed IKEv2 SA PASSED *Nov 24 07:57:56.990: IKEv2:(SESSION ID = 1,SA ID = 1):Completed SA init exchange *Nov 24 07:57:56.990: IKEv2:(SESSION ID = 1,SA ID = 1):Check for EAP exchange *Nov 24 07:57:56.991: IKEv2:(SESSION ID = 1,SA ID = 1):Generate my authentication data *Nov 24 07:57:56.991: IKEv2:(SESSION ID = 1,SA ID = 1):Use preshared key for id 209.165.200.242, key len 16 *Nov 24 07:57:56.991: IKEv2:(SESSION ID = 1,SA ID = 1):[IKEv2 -> Crypto Engine] Generate IKEv2 authentication data *Nov 24 07:57:56.991: IKEv2:(SESSION ID = 1,SA ID = 1):[Crypto Engine -> IKEv2] IKEv2 authentication data generation PASSED *Nov 24 07:57:56.992: IKEv2:(SESSION ID = 1,SA ID = 1):Get my authentication method *Nov 24 07:57:56.992: IKEv2:(SESSION ID = 1,SA ID = 1):My authentication method is 'PSK' *Nov 24 07:57:56.992: IKEv2:(SESSION ID = 1,SA ID = 1):Check for EAP exchange *Nov 24 07:57:56.993: IKEv2:(SESSION ID = 1,SA ID = 1):Generating IKE_AUTH message *Nov 24 07:57:56.994: IKEv2:(SESSION ID = 1,SA ID = 1):Constructing IDi payload: '209 BRANCH#.165.200.242' of type 'IPv4 address' *Nov 24 07:57:56.994: IKEv2:(SESSION ID = 1,SA ID = 1):ESP Proposal: 1, SPI size: 4 (IPSec negotiation), Num. transforms: 2 AES-CBC Don't use ESN *Nov 24 07:57:56.995: IKEv2:(SESSION ID = 1,SA ID = 1):Building packet for encryption. Payload contents: VID IDi AUTH SA TSi TSr NOTIFY(INITIAL_CONTACT) NOTIFY(SET_WINDOW_SIZE) NOTIFY(ESP_TFC_NO_SUPPORT) NOTIFY(NON_FIRST_FRAGS) *Nov 24 07:57:56.997: IKEv2:(SESSION ID = 1,SA ID = 1):Sending Packet [To 209.165.200.226:500/From 209.165.200.242:500/VRF i0:f0] Initiator SPI : 2BD7494C28C698F0 - Responder SPI : 3B5D666A9F360298 Message id: 1 IKEv2 IKE_AUTH Exchange REQUEST Payload contents: ENCR *Nov 24 07:57:57.062: IKEv2:(SESSION ID = 1,SA ID = 1):Received Packet [From 209.165.200.226:500/To 209.165.200.242:500/VRF i0:f0] Initiator SPI : 2BD7494C28C698F0 - Responder SPI : 3B5D666A9F360298 Message id: 1 IKEv2 IKE_AUTH Exchange RESPONSE Payload contents: VID IDr AUTH SA TSi TSr NOTIFY(SET_WINDOW_SIZE) NOTIFY(ESP_TFC_NO_SUPPORT) NOTIFY(NON_FIRST_FRAGS) *Nov 24 07:57:57.066: IKEv2:(SESSION ID = 1,SA ID = 1):Process auth response notify *Nov 24 07:57:57.068: IKEv2:(SESSION ID = 1,SA ID = 1):Searching policy based on peer's identity '209.165.200.226' of type 'IPv4 address' *Nov 24 07:57:57.070: IKEv2:(SESSION ID = 1,SA ID = 1):Searching Policy with fvrf 0, local address 209.165.200.242 *Nov 24 07:57:57.070: IKEv2:(SESSION ID = 1,SA ID = 1):Found Policy 'BRANQ_TO_HQ_POLICY' *Nov 24 07:57:57.071: IKEv2:(SESSION ID = 1,SA ID = 1):Verify peer's policy *Nov 24 07:57:57.072: IKEv2:(SESSION ID = 1,SA ID = 1):Peer's policy verified *Nov 24 07:57:57.072: IKEv2:(SESSION ID = 1,SA ID = 1):Get peer's authentication method *Nov 24 07:57:57.073: IKEv2:(SESSION ID = 1,SA ID = 1):Peer's authentication method is 'PSK' *Nov 24 07:57:57.073: IKEv2:(SESSION ID = 1,SA ID = 1):Get peer's preshared key for 209.165.200.226 *Nov 24 07:57:57.074: IKEv2:(SESSION ID = 1,SA ID = 1):Verify peer's authentication data *Nov 24 07:57:57.074: IKEv2:(SESSION ID = 1,SA ID = 1):Use preshared key for id 209.165.200.226, key len 16 *Nov 24 07:57:57.074: IKEv2:(SESSION ID = 1,SA ID = 1):[IKEv2 -> Crypto Engine] Generate IKEv2 authentication data *Nov 24 07:57:57.074: IKEv2:(SESSION ID = 1,SA ID = 1):[Crypto Engine -> IKEv2] IKEv2 authentication data generation PASSED *Nov 24 07:57:57.075: IKEv2:(SESSION ID = 1,SA ID = 1):Verification of peer's authenctication data PASSED *Nov 24 07:57:57.075: IKEv2:(SESSION ID = 1,SA ID = 1):Check for EAP exchange *Nov 24 07:57:57.077: IKEv2:(SESSION ID = 1,SA ID = 1):Processing IKE_AUTH message *Nov 24 07:57:57.090: IKEv2:(SESSION ID = 1,SA ID = 1):IPSec policy validate request sent for profile IKE_BRANCH_TO_HQ_PROFILE with psh index 1. *Nov 24 07:57:57.098: IKEv2:(SESSION ID = 1,SA ID = 1):(SA ID = 1):[IPsec -> IKEv2] Callback received for the validate proposal - PASSED. *Nov 24 07:57:57.101: IKEv2:(SESSION ID = 1,SA ID = 1):IKEV2 SA created; inserting SA into database. SA lifetime timer (86400 sec) started *Nov 24 07:57:57.101: IKEv2:(SESSION ID = 1,SA ID = 1):Session with IKE ID PAIR (209.165.200.226, 209.165.200.242) is UP *Nov 24 07:57:57.102: IKEv2:(SESSION ID = 0,SA ID = 0):IKEv2 MIB tunnel started, tunnel index 1 *Nov 24 07:57:57.103: IKEv2:(SESSION ID = 1,SA ID = 1):Load IPSEC key material *Nov 24 07:57:57.104: IKEv2:(SESSION ID = 1,SA ID = 1):(SA ID = 1):[IKEv2 -> IPsec] Create IPsec SA into IPsec database *Nov 24 07:57:57.295: IKEv2:(SESSION ID = 1,SA ID = 1):(SA ID = 1):[IPsec -> IKEv2] Creation of IPsec SA into IPsec database PASSED *Nov 24 07:57:57.297: IKEv2:(SESSION ID = 1,SA ID = 1):Checking for duplicate IKEv2 SA *Nov 24 07:57:57.297: IKEv2:(SESSION ID = 1,SA ID = 1):No duplicate IKEv2 SA found
Configurations
Full list of router configs
For Branch
!
! Last configuration change at 07:11:00 UTC Wed Nov 24 2021
!
version 16.12
service timestamps debug datetime msec
service timestamps log datetime msec
service call-home
platform qfp utilization monitor load 80
no platform punt-keepalive disable-kernel-core
platform console serial
!
hostname BRANCH
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
call-home
! If contact email address in call-home is configured as sch-smart-licensing@cisco.com
! the email address configured in Cisco Smart License Portal will be used as contact email address to send SCH notifications.
contact-email-addr sch-smart-licensing@cisco.com
profile "CiscoTAC-1"
active
destination transport-method http
no destination transport-method email
!
!
!
!
!
!
!
!
ip dhcp pool LNA
!
ip dhcp pool LAN
network 192.168.1.0 255.255.255.0
default-router 192.168.1.1
!
!
!
login on-success log
!
!
!
!
!
!
!
subscriber templating
!
!
!
!
!
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
!
!
!
!
!
!
!
crypto pki trustpoint TP-self-signed-1692966786
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-1692966786
revocation-check none
rsakeypair TP-self-signed-1692966786
!
crypto pki trustpoint SLA-TrustPoint
enrollment pkcs12
revocation-check crl
!
!
crypto pki certificate chain TP-self-signed-1692966786
certificate self-signed 01
30820330 30820218 A0030201 02020101 300D0609 2A864886 F70D0101 05050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 31363932 39363637 3836301E 170D3231 31313233 31313438
32325A17 0D333030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D31 36393239
36363738 36308201 22300D06 092A8648 86F70D01 01010500 0382010F 00308201
0A028201 0100AC78 0263FCBB A36DCA46 9E83CD43 6B12648B 15D89008 C78131DD
DE7CD9E5 76A3A77A 554429DB 88559F97 28F48190 F89D05EF 4DABC68B B2976E58
E1B3C266 E0B34ACD 22D3B143 29DB0C98 034843F4 6E7E0AA5 99B0192E 8D9668F7
8F5688F1 ED963717 34A81479 A9F0BB19 B8EE3203 E7DCAF65 AB8407DC 18730BE2
2A73775A CBDC4450 1DC3329A 76FD6D19 AE142439 0CCE644B 44CAE757 BB347977
817B3E4F F6AAD30A A724787A 506BD27F CA9C1530 EA2003E6 42363438 2AC8C38D
FFA81F55 69B7FDD5 C591C4E5 50D6CAA7 B3439190 4E22C2DD 4FC20649 9ADB8239
58409D9C 95DC5D7F 59968E1B 1032E29D 98168717 EEEC6677 EB5464C5 BBCFE607
F7720490 EFE90203 010001A3 53305130 0F060355 1D130101 FF040530 030101FF
301F0603 551D2304 18301680 14FC72D6 63F844E0 C68FDB10 0B62493F F8946303
33301D06 03551D0E 04160414 FC72D663 F844E0C6 8FDB100B 62493FF8 94630333
300D0609 2A864886 F70D0101 05050003 82010100 588E088C A2A0285A 238A7314
9783BC7F 5AE13280 755F0A98 EF6E81F2 1F1A3A60 05B77182 E08FCC48 E3D9F82D
A4CA6CD0 B3A1395C 45A5EF29 DA374102 3C131749 90AFCD34 8685793E 4154F8BC
CDC6DB32 5E8EE553 ED147BB7 63417359 7FBA926F 402AB4DC 9B2C69D2 07953357
E9A0CA14 5AE92293 2081E0EA F751AE90 4FDE45F9 FB682A2E 58DE4F0E 108CBF14
1B0C0712 3FFF5703 8A5D89A0 BA9E71F5 F6280D8C 784B2B07 F48CADD1 A6BDCFA8
1AC070D9 2A6F4F0A D2B7AE67 3FD42F0E E8BE96F6 C89CDE73 B5ED8C5A 4E69992C
78064B33 A9420ED3 701AF7A6 3BDEA5C0 2F4E0B56 0AC6629D 86277E9F 21DBB1C2
11598CB6 523E3D86 D2D64662 DF9AC5A6 41976A74
quit
crypto pki certificate chain SLA-TrustPoint
certificate ca 01
30820321 30820209 A0030201 02020101 300D0609 2A864886 F70D0101 0B050030
32310E30 0C060355 040A1305 43697363 6F312030 1E060355 04031317 43697363
6F204C69 63656E73 696E6720 526F6F74 20434130 1E170D31 33303533 30313934
3834375A 170D3338 30353330 31393438 34375A30 32310E30 0C060355 040A1305
43697363 6F312030 1E060355 04031317 43697363 6F204C69 63656E73 696E6720
526F6F74 20434130 82012230 0D06092A 864886F7 0D010101 05000382 010F0030
82010A02 82010100 A6BCBD96 131E05F7 145EA72C 2CD686E6 17222EA1 F1EFF64D
CBB4C798 212AA147 C655D8D7 9471380D 8711441E 1AAF071A 9CAE6388 8A38E520
1C394D78 462EF239 C659F715 B98C0A59 5BBB5CBD 0CFEBEA3 700A8BF7 D8F256EE
4AA4E80D DB6FD1C9 60B1FD18 FFC69C96 6FA68957 A2617DE7 104FDC5F EA2956AC
7390A3EB 2B5436AD C847A2C5 DAB553EB 69A9A535 58E9F3E3 C0BD23CF 58BD7188
68E69491 20F320E7 948E71D7 AE3BCC84 F10684C7 4BC8E00F 539BA42B 42C68BB7
C7479096 B4CB2D62 EA2F505D C7B062A4 6811D95B E8250FC4 5D5D5FB8 8F27D191
C55F0D76 61F9A4CD 3D992327 A8BB03BD 4E6D7069 7CBADF8B DF5F4368 95135E44
DFC7C6CF 04DD7FD1 02030100 01A34230 40300E06 03551D0F 0101FF04 04030201
06300F06 03551D13 0101FF04 05300301 01FF301D 0603551D 0E041604 1449DC85
4B3D31E5 1B3E6A17 606AF333 3D3B4C73 E8300D06 092A8648 86F70D01 010B0500
03820101 00507F24 D3932A66 86025D9F E838AE5C 6D4DF6B0 49631C78 240DA905
604EDCDE FF4FED2B 77FC460E CD636FDB DD44681E 3A5673AB 9093D3B1 6C9E3D8B
D98987BF E40CBD9E 1AECA0C2 2189BB5C 8FA85686 CD98B646 5575B146 8DFC66A8
467A3DF4 4D565700 6ADF0F0D CF835015 3C04FF7C 21E878AC 11BA9CD2 55A9232C
7CA7B7E6 C1AF74F6 152E99B7 B1FCF9BB E973DE7F 5BDDEB86 C71E3B49 1765308B
5FB0DA06 B92AFE7F 494E8A9E 07B85737 F3A58BE1 1A48A229 C37C1E69 39F08678
80DDCD16 D6BACECA EEBC7CF9 8428787B 35202CDC 60E4616A B623CDBD 230E3AFB
418616A9 4093E049 4D10AB75 27E86F73 932E35B5 8862FDAE 0275156F 719BB2F0
D697DF7F 28
quit
!
license udi pid CSR1000V sn 9ZHMMJIHRB3
diagnostic bootup level minimal
memory free low-watermark processor 72406
!
!
spanning-tree extend system-id
!
!
redundancy
!
crypto ikev2 proposal BRANCH_TO_HQ_IKEV2_PROPOSAL
encryption aes-gcm-256
prf sha512
group 21
crypto ikev2 proposal MY_IKEV2_PROPOSAL
encryption aes-gcm-256
prf sha512
group 21
!
crypto ikev2 policy BRANQ_TO_HQ_POLICY
proposal MY_IKEV2_PROPOSAL
!
crypto ikev2 keyring KEYRING_1
peer HQ_ROUTER
address 209.165.200.226
pre-shared-key MY_PASS_cisco123
!
!
!
crypto ikev2 profile IKE_BRANCH_TO_HQ_PROFILE
match address local 209.165.200.242
match identity remote address 209.165.200.226 255.255.255.248
authentication remote pre-share
authentication local pre-share
keyring local KEYRING_1
!
!
!
!
!
!
!
!
!
!
!
!
crypto ipsec transform-set IPSEC_TR_SET esp-aes 256
mode tunnel
!
!
!
crypto map MY_MAP 10 ipsec-isakmp
set peer 209.165.200.226
set transform-set IPSEC_TR_SET
set ikev2-profile IKE_BRANCH_TO_HQ_PROFILE
match address ACL
!
!
!
!
!
!
!
!
interface GigabitEthernet1
ip address 192.168.1.1 255.255.255.0
ip nat inside
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet2
ip address 209.165.200.242 255.255.255.248
ip nat outside
negotiation auto
no mop enabled
no mop sysid
crypto map MY_MAP
!
interface GigabitEthernet3
no ip address
shutdown
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet4
no ip address
shutdown
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet5
no ip address
shutdown
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet6
no ip address
shutdown
negotiation auto
no mop enabled
no mop sysid
!
ip forward-protocol nd
ip http server
ip http authentication local
ip http secure-server
!
ip nat inside source list NAT interface GigabitEthernet2 overload
ip route 0.0.0.0 0.0.0.0 GigabitEthernet2
ip route 0.0.0.0 0.0.0.0 GigabitEthernet2 209.165.200.241
!
ip access-list extended ACL
10 remark Preotect flows form Branch to HQ
10 permit ip 192.168.1.0 0.0.0.255 10.10.10.0 0.0.0.255 log
ip access-list extended NAT
10 deny ip 192.168.1.0 0.0.0.255 10.10.10.0 0.0.0.255 log
20 permit ip 192.168.1.0 0.0.0.255 any log
!
ip access-list standard 1
!
!
!
!
!
control-plane
!
!
!
!
!
!
line con 0
logging synchronous
stopbits 1
line vty 0 4
login
!
!
!
!
!
!
end
For ISP
!
! Last configuration change at 06:42:08 UTC Wed Nov 24 2021
!
version 16.12
service timestamps debug datetime msec
service timestamps log datetime msec
service call-home
platform qfp utilization monitor load 80
no platform punt-keepalive disable-kernel-core
platform console serial
!
hostname ISP
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
call-home
! If contact email address in call-home is configured as sch-smart-licensing@cisco.com
! the email address configured in Cisco Smart License Portal will be used as contact email address to send SCH notifications.
contact-email-addr sch-smart-licensing@cisco.com
profile "CiscoTAC-1"
active
destination transport-method http
no destination transport-method email
!
!
!
!
!
!
!
!
!
!
login on-success log
!
!
!
!
!
!
!
subscriber templating
!
!
!
!
!
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
!
!
!
!
!
!
!
crypto pki trustpoint TP-self-signed-84122297
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-84122297
revocation-check none
rsakeypair TP-self-signed-84122297
!
crypto pki trustpoint SLA-TrustPoint
enrollment pkcs12
revocation-check crl
!
!
crypto pki certificate chain TP-self-signed-84122297
certificate self-signed 01
3082032C 30820214 A0030201 02020101 300D0609 2A864886 F70D0101 05050030
2F312D30 2B060355 04031324 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 38343132 32323937 301E170D 32313131 32333131 34383235
5A170D33 30303130 31303030 3030305A 302F312D 302B0603 55040313 24494F53
2D53656C 662D5369 676E6564 2D436572 74696669 63617465 2D383431 32323239
37308201 22300D06 092A8648 86F70D01 01010500 0382010F 00308201 0A028201
0100BC1B EA84871E DA9BAEEF BD53C8A1 0105F66D CAE9AC6B 07569709 6210B4CF
FFD8ED36 2F7431C4 FE2565EB 02A6AA8D 4099724F FEE3CEED 823635BE 66D19D68
83E8744E FC42CAB2 97D7AACC 0325D0FE E352E09C 8EA65351 C317B6FE 41A8D6CD
A08BD119 4F7AB56A 07CCF83C C08991A7 15DA17CE 67AFC7D7 B10A84A8 0BC9C477
9CEE310F 96002052 3FD580B3 5D3BB1A8 C31D15D0 29181F20 93A5A5F1 7D3D7F53
24A6B5A8 25D38DA0 6C9B8E7F 8A7BDC17 D7001191 22128800 232D7E9C 918439F5
1A150E69 31C793E4 CEA0C336 48DEDDBC D2B88993 55C238A2 477D7FEF 1AE1AA2E
CFEC6C07 8E7E8ADE 33A6BDFD 39250AE9 3C63580D 5C2F3EB3 00816021 2118007C
FA010203 010001A3 53305130 0F060355 1D130101 FF040530 030101FF 301F0603
551D2304 18301680 14272A1A 0F8C1D60 49DD1FC1 C188BDEC 60FAA291 97301D06
03551D0E 04160414 272A1A0F 8C1D6049 DD1FC1C1 88BDEC60 FAA29197 300D0609
2A864886 F70D0101 05050003 82010100 671CB932 05AA4F7F 11A5144B D0E37F9B
1B6D4DA5 CEC565C7 09F23564 AFAFB3DA 09408C51 07A9ADF9 07D7B639 E9692A48
295FC5B9 DD2CE7F1 535F2380 704DEA1C A47D9DF0 F7426291 C2AF399F 1C91C4FB
FBBEA1AD 8F83D569 D488E270 3325A683 61FD35F5 633C932C D53FDB27 FA82B5A0
EA819297 78D015F9 BB13F895 C925CB78 4F91BE45 7A10FDD7 7415BFD8 92230FB2
695A3E0D CA5A1ED6 E7DA0663 B4B23E07 3E24F02C DF222F67 6D29C594 BCD31659
44606926 52218BA8 932CF6B2 B12E2C71 D9D54FBA 9CDE90E9 D2DC2A06 9D4D644B
C75558C1 BBD24B95 1D610432 FE64615A E6A6BBE7 85A485DD 48230FF0 7D2EC27F
206F136A C4CA6717 E2B10B2D B7A475E8
quit
crypto pki certificate chain SLA-TrustPoint
certificate ca 01
30820321 30820209 A0030201 02020101 300D0609 2A864886 F70D0101 0B050030
32310E30 0C060355 040A1305 43697363 6F312030 1E060355 04031317 43697363
6F204C69 63656E73 696E6720 526F6F74 20434130 1E170D31 33303533 30313934
3834375A 170D3338 30353330 31393438 34375A30 32310E30 0C060355 040A1305
43697363 6F312030 1E060355 04031317 43697363 6F204C69 63656E73 696E6720
526F6F74 20434130 82012230 0D06092A 864886F7 0D010101 05000382 010F0030
82010A02 82010100 A6BCBD96 131E05F7 145EA72C 2CD686E6 17222EA1 F1EFF64D
CBB4C798 212AA147 C655D8D7 9471380D 8711441E 1AAF071A 9CAE6388 8A38E520
1C394D78 462EF239 C659F715 B98C0A59 5BBB5CBD 0CFEBEA3 700A8BF7 D8F256EE
4AA4E80D DB6FD1C9 60B1FD18 FFC69C96 6FA68957 A2617DE7 104FDC5F EA2956AC
7390A3EB 2B5436AD C847A2C5 DAB553EB 69A9A535 58E9F3E3 C0BD23CF 58BD7188
68E69491 20F320E7 948E71D7 AE3BCC84 F10684C7 4BC8E00F 539BA42B 42C68BB7
C7479096 B4CB2D62 EA2F505D C7B062A4 6811D95B E8250FC4 5D5D5FB8 8F27D191
C55F0D76 61F9A4CD 3D992327 A8BB03BD 4E6D7069 7CBADF8B DF5F4368 95135E44
DFC7C6CF 04DD7FD1 02030100 01A34230 40300E06 03551D0F 0101FF04 04030201
06300F06 03551D13 0101FF04 05300301 01FF301D 0603551D 0E041604 1449DC85
4B3D31E5 1B3E6A17 606AF333 3D3B4C73 E8300D06 092A8648 86F70D01 010B0500
03820101 00507F24 D3932A66 86025D9F E838AE5C 6D4DF6B0 49631C78 240DA905
604EDCDE FF4FED2B 77FC460E CD636FDB DD44681E 3A5673AB 9093D3B1 6C9E3D8B
D98987BF E40CBD9E 1AECA0C2 2189BB5C 8FA85686 CD98B646 5575B146 8DFC66A8
467A3DF4 4D565700 6ADF0F0D CF835015 3C04FF7C 21E878AC 11BA9CD2 55A9232C
7CA7B7E6 C1AF74F6 152E99B7 B1FCF9BB E973DE7F 5BDDEB86 C71E3B49 1765308B
5FB0DA06 B92AFE7F 494E8A9E 07B85737 F3A58BE1 1A48A229 C37C1E69 39F08678
80DDCD16 D6BACECA EEBC7CF9 8428787B 35202CDC 60E4616A B623CDBD 230E3AFB
418616A9 4093E049 4D10AB75 27E86F73 932E35B5 8862FDAE 0275156F 719BB2F0
D697DF7F 28
quit
!
license udi pid CSR1000V sn 9O9YM6O0JUX
diagnostic bootup level minimal
memory free low-watermark processor 72406
!
!
spanning-tree extend system-id
!
!
redundancy
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface GigabitEthernet1
no ip address
shutdown
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet2
ip address 209.165.200.241 255.255.255.248
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet3
ip address 209.165.200.225 255.255.255.248
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet4
no ip address
shutdown
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet5
no ip address
shutdown
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet6
no ip address
shutdown
negotiation auto
no mop enabled
no mop sysid
!
ip forward-protocol nd
ip http server
ip http authentication local
ip http secure-server
!
!
!
!
!
!
!
!
control-plane
!
!
!
!
!
!
line con 0
logging synchronous
stopbits 1
line vty 0 4
login
!
!
!
!
!
!
end
For HQ
!
! Last configuration change at 07:06:10 UTC Wed Nov 24 2021
!
version 16.12
service timestamps debug datetime msec
service timestamps log datetime msec
service call-home
platform qfp utilization monitor load 80
no platform punt-keepalive disable-kernel-core
platform console serial
!
hostname HQ
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
call-home
! If contact email address in call-home is configured as sch-smart-licensing@cisco.com
! the email address configured in Cisco Smart License Portal will be used as contact email address to send SCH notifications.
contact-email-addr sch-smart-licensing@cisco.com
profile "CiscoTAC-1"
active
destination transport-method http
no destination transport-method email
!
!
!
!
!
!
!
!
ip dhcp pool LAN_HQ
network 10.10.10.0 255.255.255.0
default-router 10.10.10.1
!
!
!
login on-success log
!
!
!
!
!
!
!
subscriber templating
!
!
!
!
!
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
!
!
!
!
!
!
!
crypto pki trustpoint TP-self-signed-2324770154
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-2324770154
revocation-check none
rsakeypair TP-self-signed-2324770154
!
crypto pki trustpoint SLA-TrustPoint
enrollment pkcs12
revocation-check crl
!
!
crypto pki certificate chain TP-self-signed-2324770154
certificate self-signed 01
30820330 30820218 A0030201 02020101 300D0609 2A864886 F70D0101 05050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 32333234 37373031 3534301E 170D3231 31313233 31313438
31345A17 0D333030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D32 33323437
37303135 34308201 22300D06 092A8648 86F70D01 01010500 0382010F 00308201
0A028201 0100938C 016D04E5 1DECD707 D9368E3E 6FD2D095 41A6B9CD BF8F4B04
410CDA5D 01C0E98E 25E7B2C9 8F53E150 7D8B24B4 37EEE62C 18847208 3510C9F0
2F56E835 383873CF 5209BE1A AD7523B3 55DC5DE5 BC0B0CCC 1C8FAC6E 60941FFA
477744DD D36523DA BCFF508A E9D46CC2 C77052E8 917FAA50 27258E7A CFD09AF3
7CB0528F 454E2CDF 321CB8BF D598F518 73E26720 79332134 F02B588C 9D90D3F3
DB1C2B89 4932A304 42138B8E B5AD6F79 E965D44B 4E632B00 E79BBFD1 7E08AEF4
0A9B8076 1C1B9C1E DA5C09A2 B4E5312F F8467A64 C1FF6988 DCBBBCAB BEA34222
CCFC6629 360058AD 39002B80 EE6B139E A3BF0842 74AF2D9E 05F292FD F14D33A1
B2FA4C9F 06770203 010001A3 53305130 0F060355 1D130101 FF040530 030101FF
301F0603 551D2304 18301680 14714B38 507B01A9 A7102D01 D5E1B173 EDA1D582
65301D06 03551D0E 04160414 714B3850 7B01A9A7 102D01D5 E1B173ED A1D58265
300D0609 2A864886 F70D0101 05050003 82010100 8735E97C B93FB566 8C5209CD
23B62305 9ABBA953 57C732B1 666BE200 46BFF2D9 9EDFF708 6E9709C6 2366C61F
37C3A528 99143331 0155150B C8ACB4E1 A103689A AEB199D0 237591BF 96DD5A6A
BB393CD5 B38F546C B4FD3EFD 2683113C B5002459 4C6CACF1 405C1752 330576BF
6940957B BB6EFDE1 77C767BA B16B65FB 7A5CA633 6ADA8B00 2EF100BA 655FDE75
1B275E6F 0130BD58 1E103BF3 671A3E9F 4789424F 9E7B0F5A 9A9081C3 D4ADFBE4
775B7C7D C5C9BD5C 745A324E 06567E33 73A94713 7CBBF58A 395CC1BB A3AF6D51
7EDA57D2 CADFE3AF 90930500 5ADA83AD BFD3B51B 1DC1E559 EBC9780C B03AD42D
FA481F67 27545F3A 5FFCDA3B 54F46817 FF169F48
quit
crypto pki certificate chain SLA-TrustPoint
certificate ca 01
30820321 30820209 A0030201 02020101 300D0609 2A864886 F70D0101 0B050030
32310E30 0C060355 040A1305 43697363 6F312030 1E060355 04031317 43697363
6F204C69 63656E73 696E6720 526F6F74 20434130 1E170D31 33303533 30313934
3834375A 170D3338 30353330 31393438 34375A30 32310E30 0C060355 040A1305
43697363 6F312030 1E060355 04031317 43697363 6F204C69 63656E73 696E6720
526F6F74 20434130 82012230 0D06092A 864886F7 0D010101 05000382 010F0030
82010A02 82010100 A6BCBD96 131E05F7 145EA72C 2CD686E6 17222EA1 F1EFF64D
CBB4C798 212AA147 C655D8D7 9471380D 8711441E 1AAF071A 9CAE6388 8A38E520
1C394D78 462EF239 C659F715 B98C0A59 5BBB5CBD 0CFEBEA3 700A8BF7 D8F256EE
4AA4E80D DB6FD1C9 60B1FD18 FFC69C96 6FA68957 A2617DE7 104FDC5F EA2956AC
7390A3EB 2B5436AD C847A2C5 DAB553EB 69A9A535 58E9F3E3 C0BD23CF 58BD7188
68E69491 20F320E7 948E71D7 AE3BCC84 F10684C7 4BC8E00F 539BA42B 42C68BB7
C7479096 B4CB2D62 EA2F505D C7B062A4 6811D95B E8250FC4 5D5D5FB8 8F27D191
C55F0D76 61F9A4CD 3D992327 A8BB03BD 4E6D7069 7CBADF8B DF5F4368 95135E44
DFC7C6CF 04DD7FD1 02030100 01A34230 40300E06 03551D0F 0101FF04 04030201
06300F06 03551D13 0101FF04 05300301 01FF301D 0603551D 0E041604 1449DC85
4B3D31E5 1B3E6A17 606AF333 3D3B4C73 E8300D06 092A8648 86F70D01 010B0500
03820101 00507F24 D3932A66 86025D9F E838AE5C 6D4DF6B0 49631C78 240DA905
604EDCDE FF4FED2B 77FC460E CD636FDB DD44681E 3A5673AB 9093D3B1 6C9E3D8B
D98987BF E40CBD9E 1AECA0C2 2189BB5C 8FA85686 CD98B646 5575B146 8DFC66A8
467A3DF4 4D565700 6ADF0F0D CF835015 3C04FF7C 21E878AC 11BA9CD2 55A9232C
7CA7B7E6 C1AF74F6 152E99B7 B1FCF9BB E973DE7F 5BDDEB86 C71E3B49 1765308B
5FB0DA06 B92AFE7F 494E8A9E 07B85737 F3A58BE1 1A48A229 C37C1E69 39F08678
80DDCD16 D6BACECA EEBC7CF9 8428787B 35202CDC 60E4616A B623CDBD 230E3AFB
418616A9 4093E049 4D10AB75 27E86F73 932E35B5 8862FDAE 0275156F 719BB2F0
D697DF7F 28
quit
!
license udi pid CSR1000V sn 9TNOH3ECZRA
diagnostic bootup level minimal
memory free low-watermark processor 72406
!
!
spanning-tree extend system-id
!
!
redundancy
!
crypto ikev2 proposal MY_IKEV2_PROPOSAL
encryption aes-gcm-256
prf sha512
group 21
!
crypto ikev2 policy HQ_TO_BRANCH_POLICY
proposal MY_IKEV2_PROPOSAL
!
crypto ikev2 keyring KEYRING_1
peer BRANCH_ROUTER
address 209.165.200.242
pre-shared-key MY_PASS_cisco123
!
!
!
crypto ikev2 profile IKE_HQ_TO_BRANCH_PROFILE
match address local 209.165.200.226
match identity remote address 209.165.200.242 255.255.255.248
authentication remote pre-share
authentication local pre-share
keyring local KEYRING_1
!
!
!
!
!
!
!
!
!
!
!
!
crypto ipsec transform-set IPSEC_TR_SET esp-aes 256
mode tunnel
!
!
!
crypto map MY_MAP 10 ipsec-isakmp
set peer 209.165.200.242
set transform-set IPSEC_TR_SET
set ikev2-profile IKE_HQ_TO_BRANCH_PROFILE
match address ACL
!
!
!
!
!
!
!
!
interface GigabitEthernet1
ip address 10.10.10.1 255.255.255.0
ip nat inside
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet2
no ip address
shutdown
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet3
ip address 209.165.200.226 255.255.255.248
ip nat outside
negotiation auto
no mop enabled
no mop sysid
crypto map MY_MAP
!
interface GigabitEthernet4
no ip address
shutdown
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet5
no ip address
shutdown
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet6
no ip address
shutdown
negotiation auto
no mop enabled
no mop sysid
!
ip forward-protocol nd
ip http server
ip http authentication local
ip http secure-server
!
ip nat inside source list NAT interface GigabitEthernet3 overload
ip route 0.0.0.0 0.0.0.0 GigabitEthernet3
ip route 0.0.0.0 0.0.0.0 GigabitEthernet3 209.165.200.225
!
ip access-list extended ACL
10 remark Preotect flows form HQ to Branch
10 permit ip 10.10.10.0 0.0.0.255 192.168.1.0 0.0.0.255 log
ip access-list extended NAT
10 deny ip 10.10.10.0 0.0.0.255 192.168.1.0 0.0.0.255 log
20 permit ip 10.10.10.0 0.0.0.255 any log
!
ip access-list standard 1
!
!
!
!
!
control-plane
!
!
!
!
!
!
line con 0
logging synchronous
stopbits 1
line vty 0 4
login
!
!
!
!
!
!
end