This guide explains how to install the dig dns tool on windows 11 in a few steps. It is just a little bit modified version of How to install DIG dns tool on windows 10 howtos.
1. First download the latest Bind9 executable for Windows. All ISC software is available at https://www.isc.org/download/. However, there is a message, that the latest win executable is 9.6.23, which we may download from the link 9.16.23.
2. When we successfully downloaded the archive file, extract the zipfile content to a temporary directory on your workstation.
3. Go to the directory and run as Administrator “BINDInstall.exe”, then choose the “Tools only” option and type the target directory where to install dig, I had chosen c:\Program Files\dig.
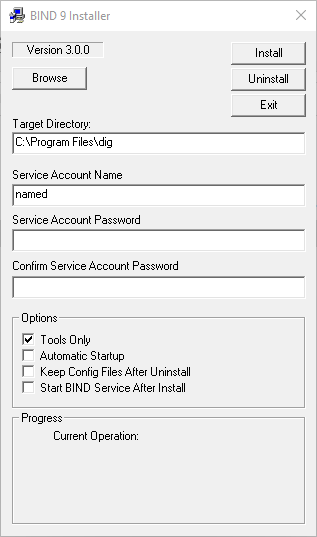
4. Click on Install, once the installer asks that directory does not exist click on Yes to create it
5. The installer then asks you if you agree to install Microsoft Visual C++ 2017 Redistributable. Click on Close and once it will ask you if you are sure, click Yes.
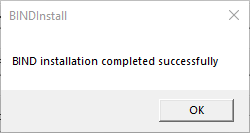
After installation, you should see positive message.
5. Next, we need to add the path of the dig folder (c:\Program Files\dig\bin) to the system PATHS variable. We should do it the following way.
6. Press Win + S and look for system environment
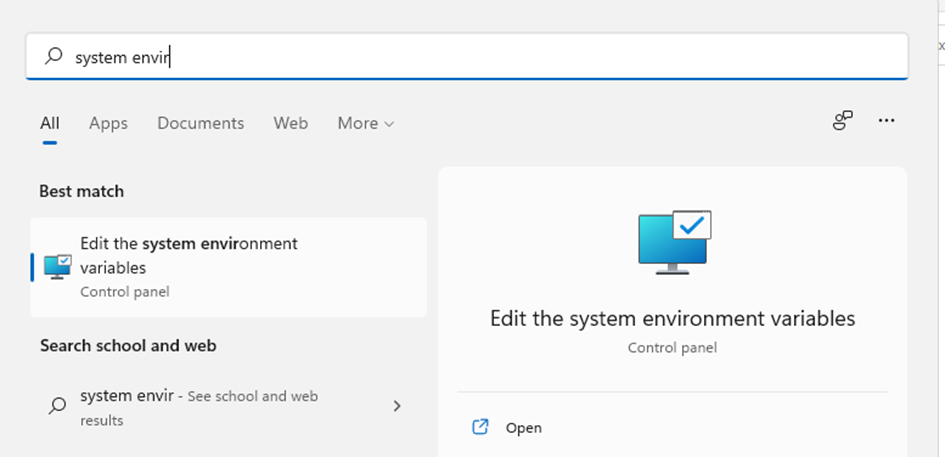
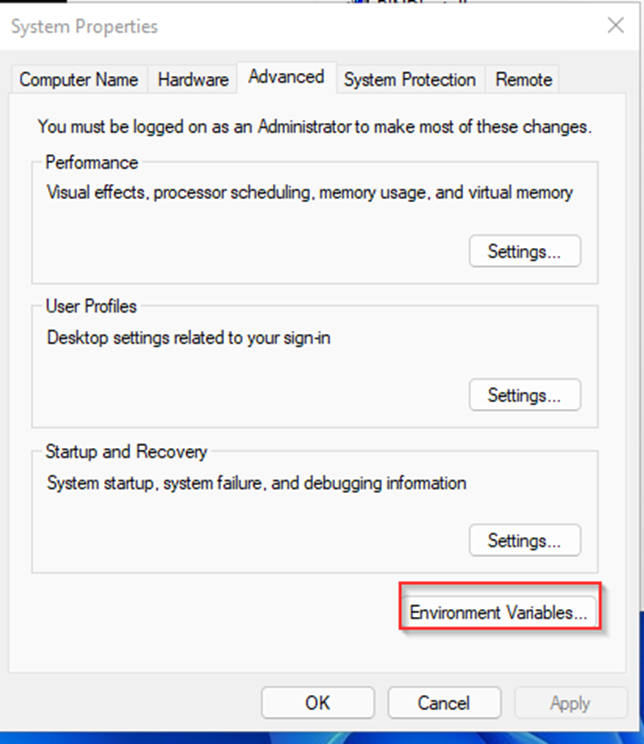
7. Then choose “Edit the system environment variable” and type admin passwd if needed. The following box will open. There is a button Environment Variables, click on it and
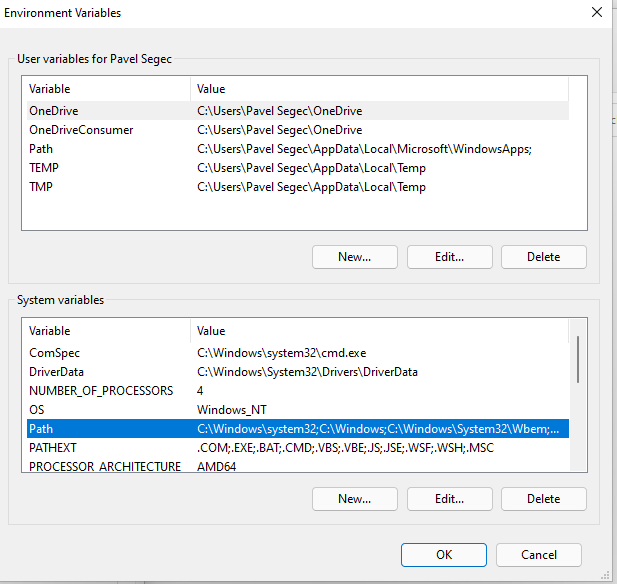
6. then double click on the Path variable of System variables, or select Path and click on Edit
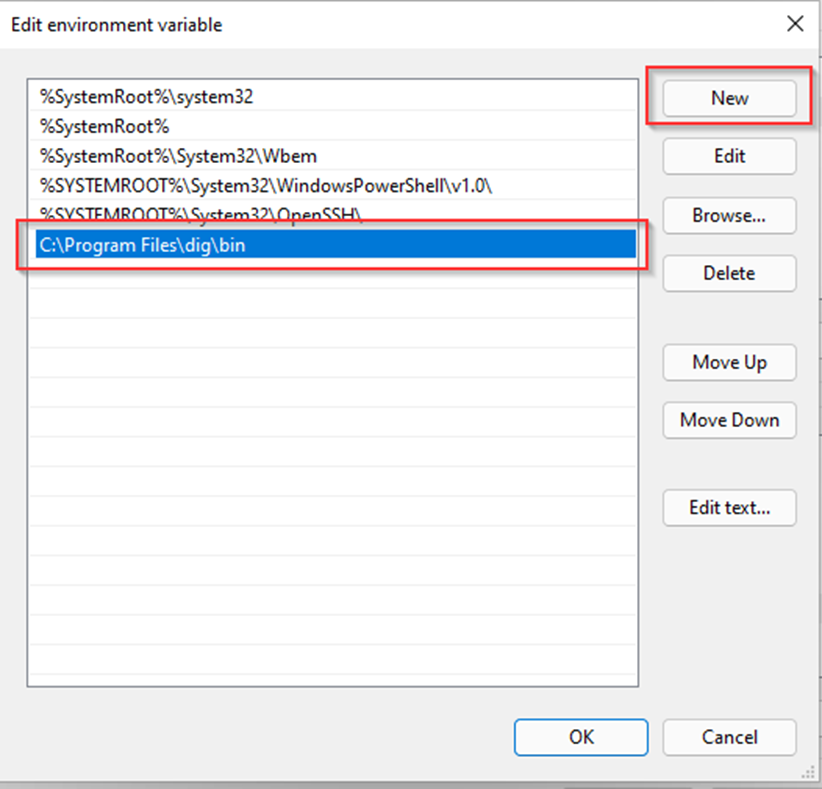
7. Following windows will appear, where we need to click on the New button and then we write the path. Clicking on Ok close the dialog. And do it twice again (Ok and Ok|
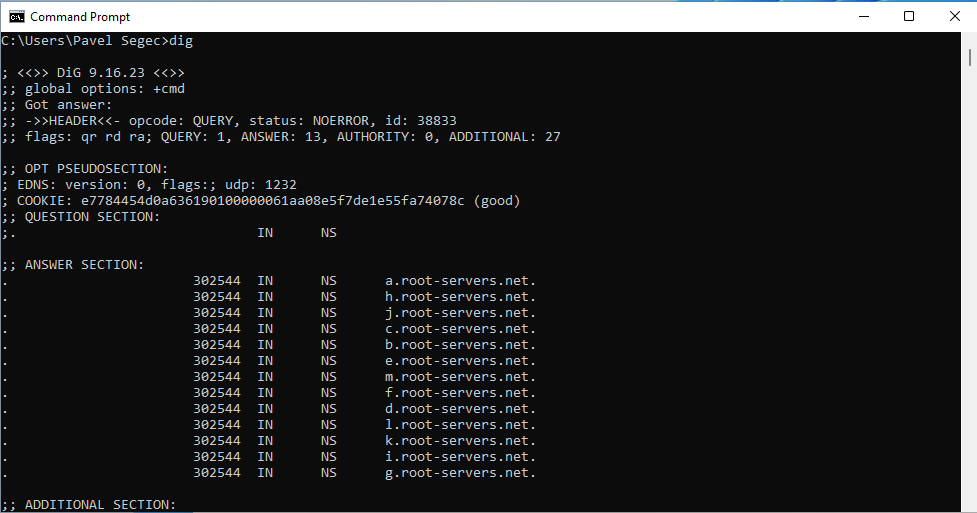
8. Now it should work. Open Command prompt and type dig